Onboard External GCCHigh or commercial User to commercial AD tenant
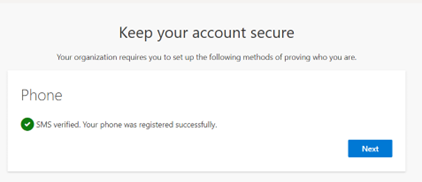
- Add users as External User in Azure AD. If You are adding a GCC or GCChigh user, you need to follow step 11 before you start step 1.
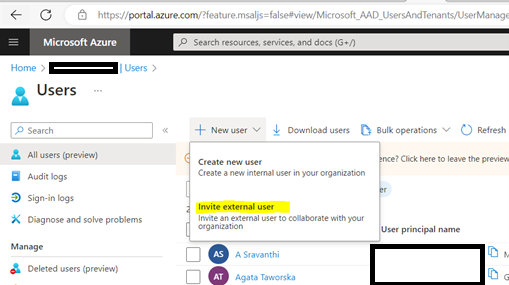
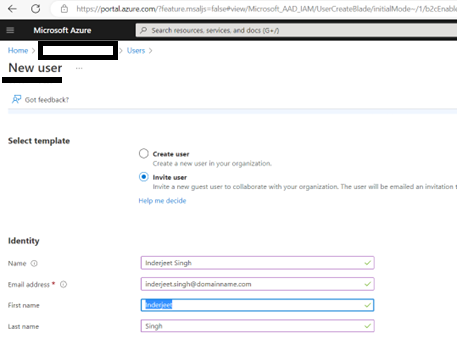
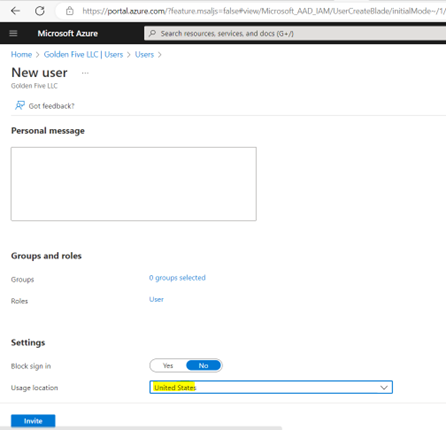
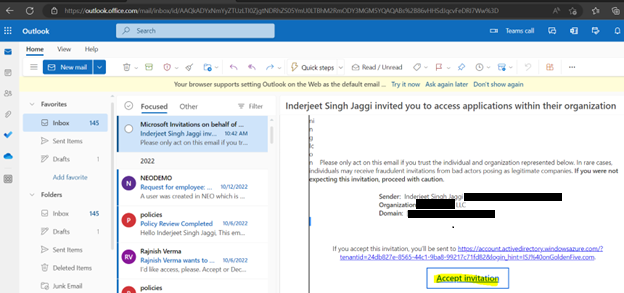
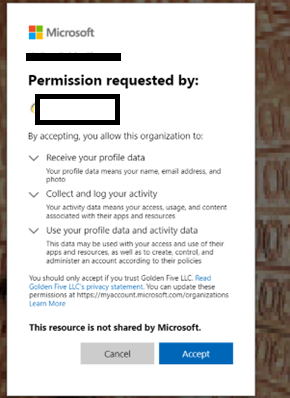
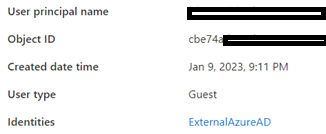
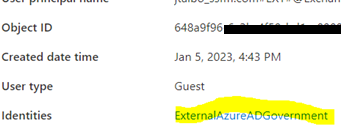
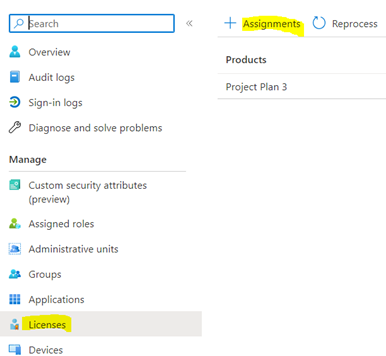
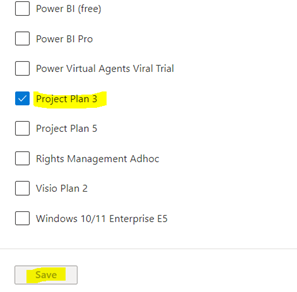
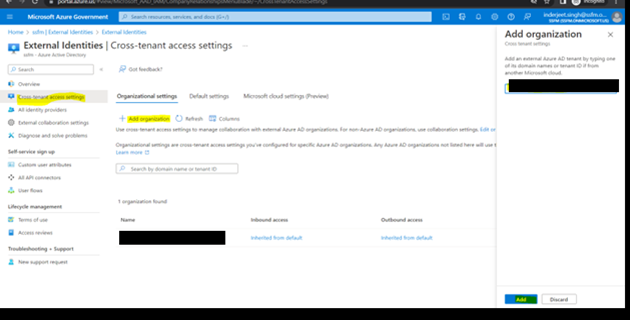
11. For GCCHigh, below tenant level setting is additionally needed before you follow step 1
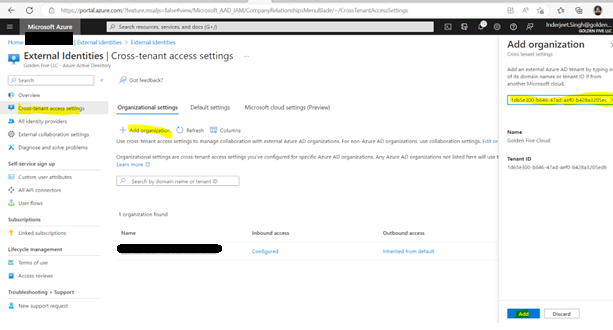
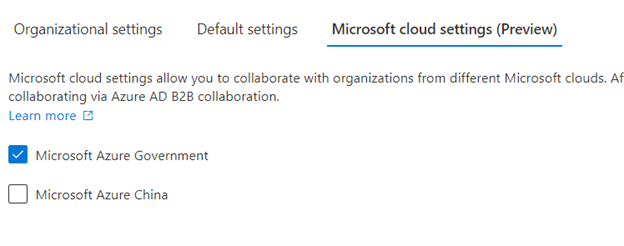
- Once added, click on ‘Inherited from default’
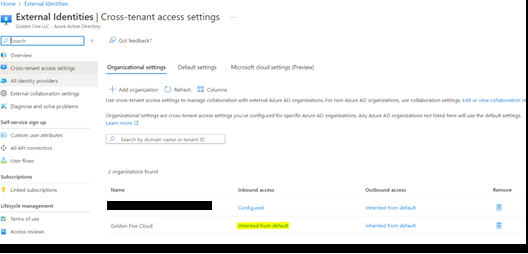
- Select ‘Customize Settings’ for B2B collaboration > ‘Allow access’ under external users and group. Set ‘Allow access’ under Applications
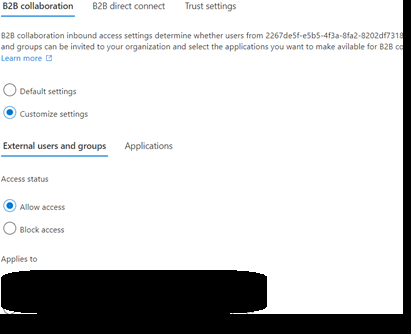
- Select ‘Customize Settings’ for B2B Direct Connect > ‘Allow access’ under external users and group. Set ‘Allow access’ under Applications
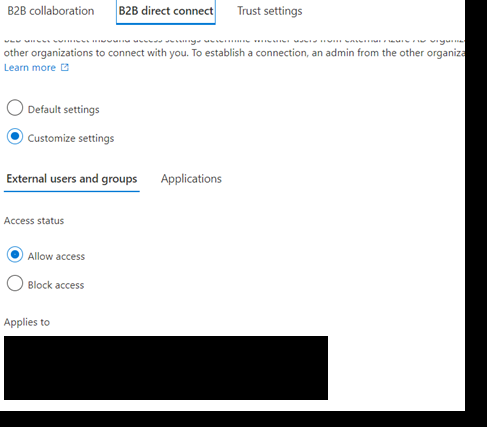
- Under Microsoft cloud settings select ‘Microsoft Azure Government’
- Now from GCCHigh, go to Access Poratl.azure.com, search Azure Active Directory > ‘External Identities’ from left navigation > Add the GCCHigh tenant ID and then select Add at bottom.
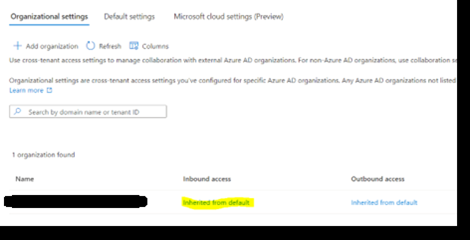
- For GCCHigh we should leave ‘Inherited from default’
- Under Microsoft cloud settings select ‘Microsoft Azure Commercial’

