Archive for July, 2023
PCI DSS 4.0 point 8.3.6 : Deploy the Windows Guest Configuration extension to enable Guest Configuration assignments on Windows VMs
While I was working on PCI DSS 4.0, I saw a VM under point 8.3.6 Deploy the Windows Guest Configuration extension to enable Guest Configuration assignments on Windows VMs. I identified that the issue to be with Guest configuration not installed on VM. To fix , we need to run open the Shell command from top right corner of the screen next to search as shown in below screenshot
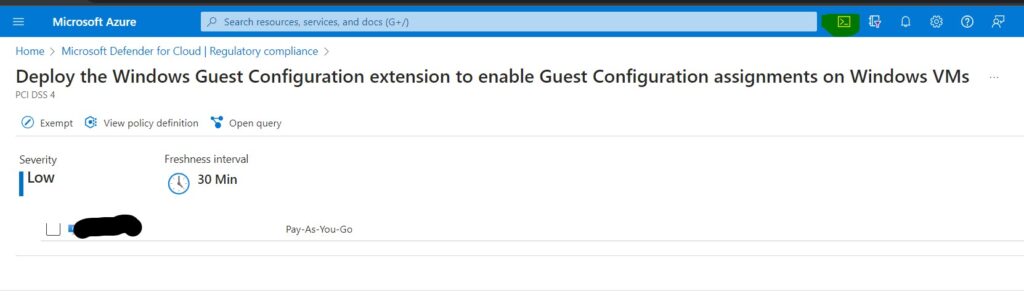
Make sure we have Bash selected and run below command in the Shell. Make sure you replace VMname and resourcename from the command.
az vm extension set --publisher Microsoft.GuestConfiguration --name ConfigurationforWindows --extension-instance-name AzurePolicyforWindows --resource-group 'Resourcename' --vm-name myVM --enable-auto-upgrade true
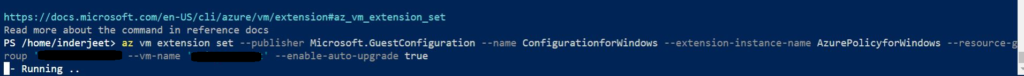
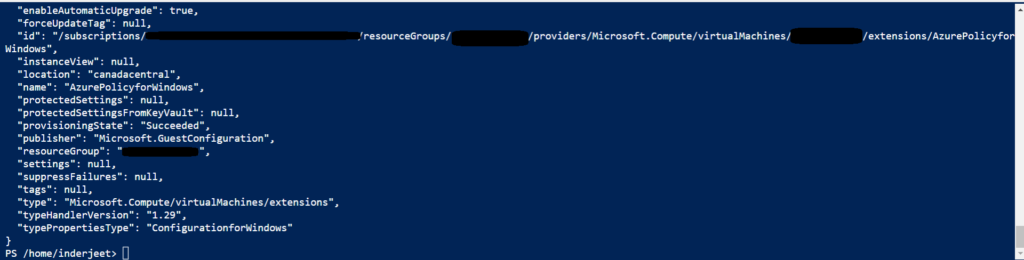
Once command is completed, wait for 24 hrs and this point will be closed in PCI DSS 4.0 Dashboard.
Thanks and Regards,
Inderjeet Singh Jaggi
After disk encryption unable to backup Virtual Machine in Azure
I recently encountered an issue that I believe is worth sharing with you. We encrypted our disk as required by PCI DSS 4.0 compliance. However, after the encryption process was completed, we started receiving an error with the code ‘UserErrorEncryptedVmNotSupportedWithDiskEx’, which indicates that ‘disk exclusion is not supported for encrypted virtual machines‘
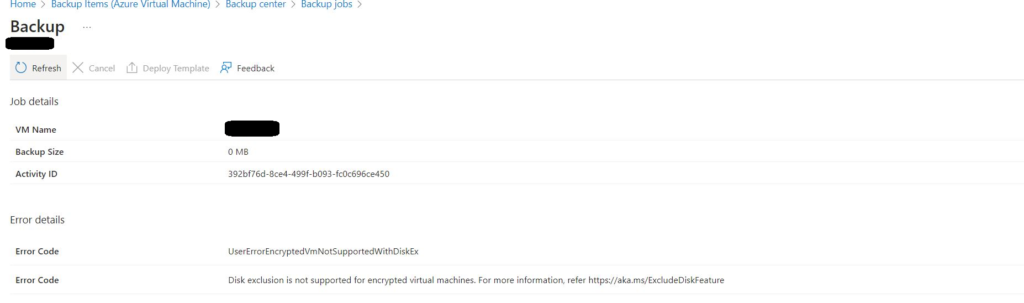
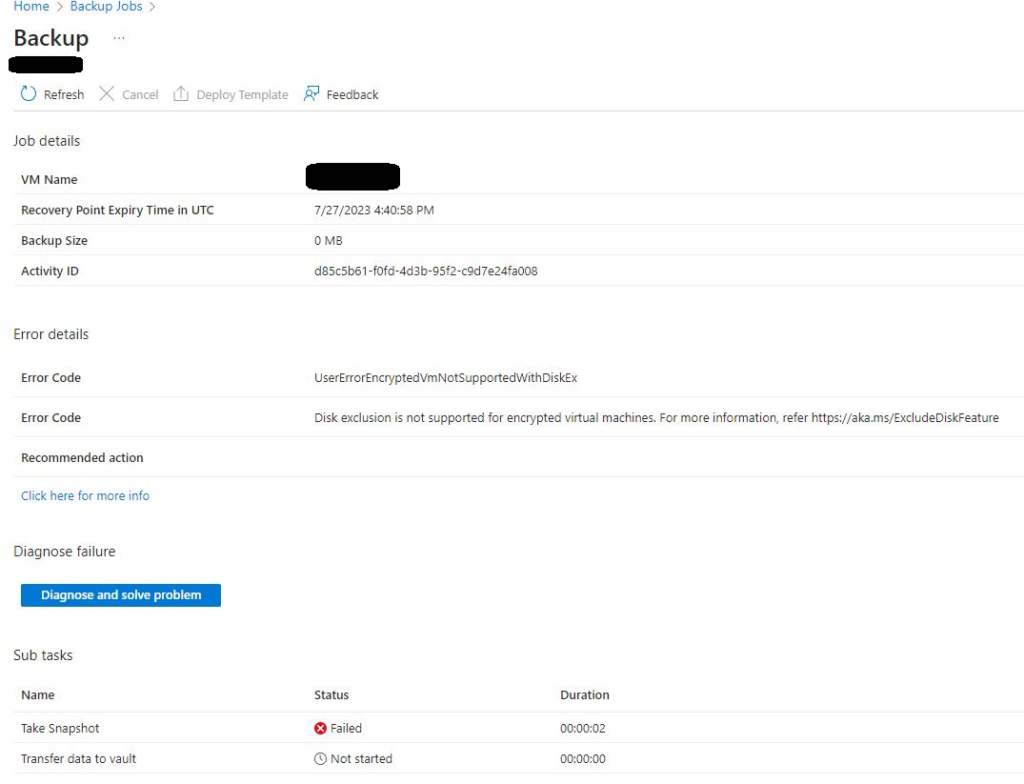
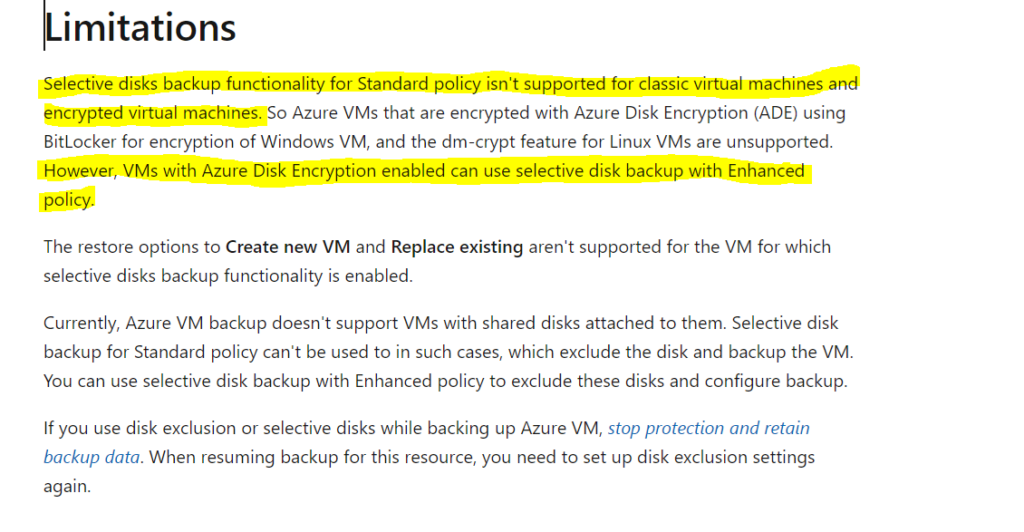
When reviewed the backend log we understood that you tried configuring selective disk backup for encrypted disk backup and this is not supported with standard backup policy, however you can configure backup with enhanced policy. I had only OS disk so this article wasn’t much helpful for me.
https://learn.microsoft.com/en-us/azure/backup/selective-disk-backup-restore#limitations
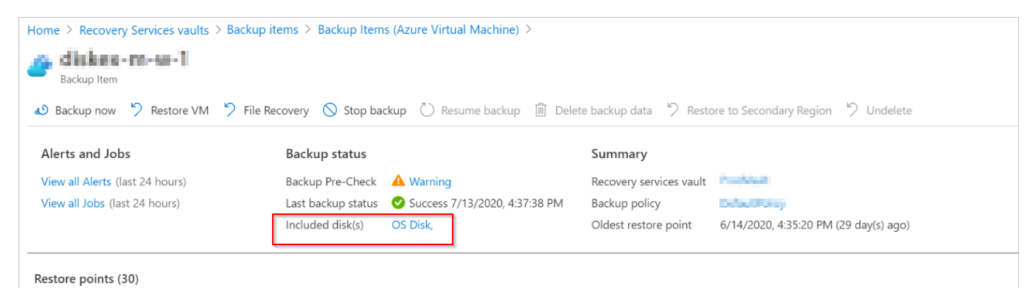
On the backup screen, I could see OS disk as included disks.
But from the log I could see you have enabled backup without selective disk backup option, and it failed with error UserErrorKeyVaultPermissionsNotConfigured
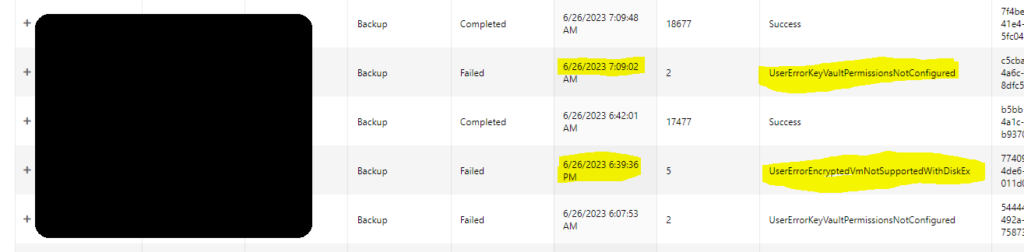
After lot of research, I found we need to run below command to fix the issue and reset the exclusion. This will mainly reset the settings.
az backup protection update-for-vm --resource-group {resourcegroup} --vault-name {vaultname} -c {vmname} -i {vmname} --disk-list-setting resetexclusionsettings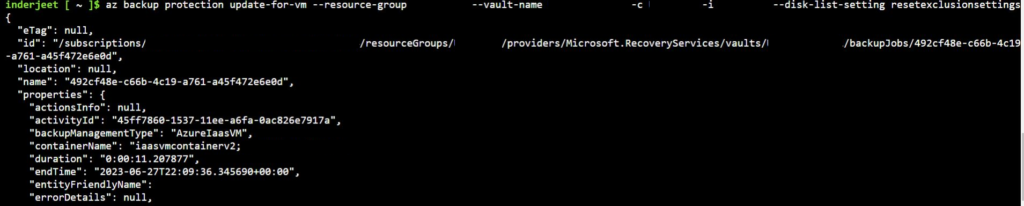
After above command, I was able to start the backup and could see the completed status of the VM’s
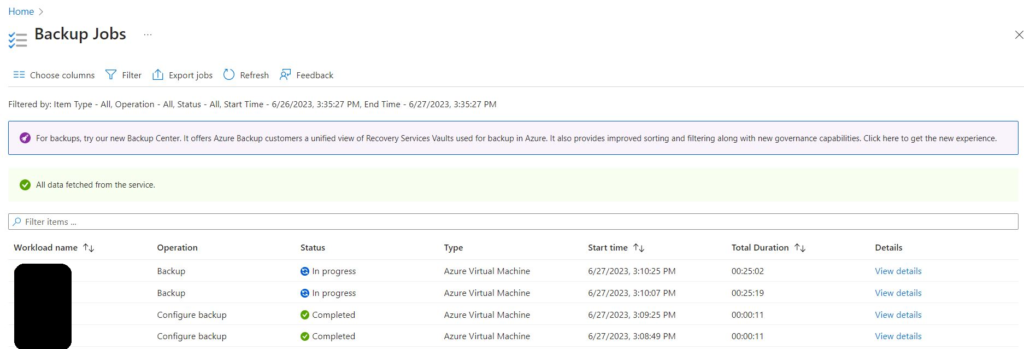
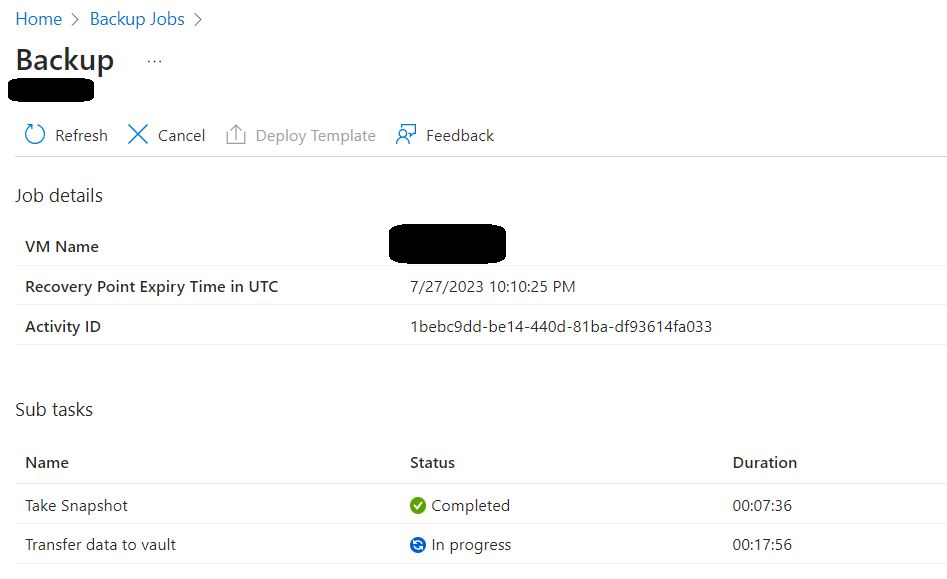
Thanks and regards,
Inderjeet Singh Jaggi
Cloud Architect – Golden Five Consulting
[email protected]
Using Office 365 for information protection and classification
“Secure Your Data with Office 365: Protect and Classify Your Information with Confidence.”
Introduction
Offering a plethora of tools for information protection, Office 365, a formidable cloud-based platform, enables organizations to fortify their data against unauthorized access, pinpoint and mitigate potential threats, and categorize data according to its degree of sensitivity. This comprehensive system empowers organizations to ensure the security and compliance of their data in line with industry standards. This comprehensive guide will delve into the multifaceted features and capabilities of Office 365 for information protection and classification.
How to Leverage Office 365 for Data Protection and Classification in Your Organization
The fundamentals of any organization’s security strategy encompass data protection and classification. As organizations transition to cloud-based systems, it becomes imperative to guarantee the security and proper categorization of their data. Microsoft Office 365 offers an extensive array of tools to assist organizations in safeguarding and classifying their data.
Office 365 encompasses a diverse suite of data protection and classification features that play a crucial role in securing and appropriately categorizing data. These encompass encryption, data loss prevention (DLP), and data classification measures.
Encryption stands as a pivotal element in safeguarding data. Office 365 incorporates encryption for data both at rest and in transit, thereby ensuring that data remains secure and exclusively accessible to authorized individuals.
Data loss prevention (DLP) represents a feature that aids organizations in shielding sensitive data from unauthorized access. Office 365 boasts a range of DLP attributes, including the capability to identify and obstruct the sharing of sensitive data beyond the organization’s confines.
Data classification serves as an integral facet of any robust security approach. Office 365 offers an assortment of tools to facilitate organizations in categorizing their data. These tools encompass the ability to label data, classify data based on its content, and establish access controls in alignment with the data’s classification.
Organizations can fortify the security and classification of their data by leveraging the features provided by Office 365. This serves to shield data from unauthorized access and guarantees its appropriate usage.
Best Practices for Using Office 365 for Information Protection and Classification
1. Implementation of a Transparent Protocol: Implement a transparent protocol for the utilization of Office 365 in safeguarding and categorizing information. Such a protocol should encompass directives for data classification, delineation of data categorization responsibilities, and measures for data fortification.
2. Leverage the multifaceted security capabilities inherent in Office 365 to bolster data integrity. These capabilities encompass thwarting data breaches, enforcing encryption protocols, and instituting multi-factor authentication for robust safeguarding.
3. Equip personnel with comprehensive training on harnessing Office 365 for upholding information security and classification. This training should encompass data categorization, protective measures, and adept utilization of the platform’s security suite.
4. Exercise vigilant oversight over data access within Office 365. This entails scrutinizing authorized personnel, the nature of their access privileges, and the temporal aspects of data retrieval.
5. Conduct meticulous audits of data repositories within Office 365 to ascertain proper classification and protective measures. This includes meticulous examination of access rights, user privileges, and temporal data interactions.
6. Continuously refine the directives governing Office 365 usage for information protection and classification. This includes updating protocols for data categorization, delineating ownership of classification duties, and fortifying data security measures.
7. Vigilantly scrutinize adherence to policies governing Office 365’s role in information protection and classification. This involves assessing policy compliance, evaluating access privileges, and monitoring data interaction patterns.
8. Respond to Breaches: Respond quickly and effectively to any breaches of data stored in Office 365. This includes identifying the source of the breach, assessing the damage, and taking steps to prevent future breaches.
Exploring the Benefits of Office 365 for Data Protection and Classification
Safeguarding and categorizing data are pivotal facets of any enterprise’s security blueprint. As the volume of electronically stored and shared data grows, entities must diligently safeguard and appropriately categorize their data. Office 365 furnishes an extensive array of tools to aid entities in safeguarding and categorizing their data.
Office 365 furnishes an assortment of data protection features, fortifying entities’ data. These encompass encryption, data loss prevention (DLP), and multi-factor authentication. Encryption shields data by obfuscating it, rendering it exclusively accessible to authorized users. DLP enables entities to pinpoint and safeguard sensitive data, such as credit card or Social Security numbers. Multi-factor authentication bolsters security by mandating additional authentication measures, like a code delivered to a user’s mobile device or a biometric scan.
Moreover, Office 365 equips entities with tools for data classification. This approach aids in pinpointing and safeguarding sensitive data, like proprietary customer details or proprietary knowledge. Office 365 provides a range of classification tools, including labels, retention policies, and data governance. Labels allow organizations to assign categories to their data, such as “confidential” or “public.” Retention policies help organizations determine how long data should be kept and when it should be deleted. Data governance helps organizations ensure that their data is properly managed and protected.
In addition to data protection and classification, Office 365 also provides a range of other security features, such as malware protection, threat intelligence, and mobile device management. These features help organizations protect their data from malicious actors and ensure that their data is secure.
Overall, Office 365 provides a comprehensive suite of tools to help organizations protect and classify their data. By leveraging these tools, organizations can ensure that their data is secure and properly managed.
How Office 365 Can Help You Classify Your Data for Compliance
Data classification is an important part of any organization’s compliance strategy. It helps organizations identify and protect sensitive data, and ensure that it is handled in accordance with applicable laws and regulations.
Office 365 provides a range of tools and features that can help organizations classify their data for compliance. These include:
Data Loss Prevention (DLP): DLP is a feature of Office 365 that helps organizations identify, monitor, and protect sensitive data. It can be used to detect and block the unauthorized sharing of sensitive data, and to ensure that data is handled in accordance with applicable laws and regulations.
Data Governance, a crucial aspect of Office 365, empowers organizations to streamline their data management. It equips them with robust mechanisms for formulating and upholding data policies, while also enabling vigilant oversight and audit of data accessibility.
Furthermore, Data Classification, another integral facet of Office 365, assists organizations in categorizing their data based on its level of confidentiality. It furnishes them with instrumental resources for crafting and enforcing data classification protocols, alongside facilitating meticulous surveillance and review of data accessibility.
Moreover, Rights Management, an indispensable feature of Office 365, supports organizations in safeguarding their data against unauthorized intrusion. It furnishes them with essential means for establishing and enforcing data access regulations, while also enabling meticulous monitoring and audit of data accessibility.
By using these features, organizations can ensure that their data is classified and handled in accordance with applicable laws and regulations. This helps organizations protect their data, and ensure that they remain compliant with applicable laws and regulations.
How Office 365 Can Help You Protect Your Sensitive Data
Office 365 represents a formidable array of cloud-based applications, offering a compelling resource for organizations seeking to safeguard their sensitive data. Its comprehensive security features are designed to fortify data against unauthorized access, malicious assaults, and potential loss.
The platform offers a secure environment for data storage and sharing, ensuring that all information housed within Office 365 is shielded by encryption and accessible solely to approved users. Moreover, Office 365 incorporates advanced security measures such as multi-factor authentication, necessitating additional validation like a mobile device-delivered code or a biometric scan to access data, thus reinforcing the system’s defense against unauthorized entry.
Moreover, Office 365 equips organizations with an array of tools for vigilant data oversight and management. From monitoring data access and user activity to setting up alerts for detecting suspicious behavior, the platform empowers organizations to swiftly pinpoint and counter potential security risks.
Furthermore, Office 365 offers a diverse set of backup and recovery mechanisms, crucial for safeguarding data in the face of calamity. Leveraging the platform, organizations can securely back up their data to the cloud, ensuring its integrity and accessibility even in the event of local system compromise.
Overall, Office 365 provides a comprehensive set of tools to help organizations protect their sensitive data. By taking advantage of Office 365’s security features, organizations can ensure that their data is safe and secure.
Conclusion
Office 365 offers a wide array of tools for safeguarding and categorizing information. It empowers organizations to shield their data from unauthorized entry, and equips them with the capability to classify and organize data for improved handling. Through Office 365, organizations can guarantee the security and proper governance of their data, while also facilitating swift and effortless data retrieval. This renders Office 365 a prime choice for organizations seeking to fortify and oversee their data.
Download a SharePoint Online Page
I encountered an issue where I needed to download a page and upload it to a new site collection. Although this issue may not be common, if you are experiencing it, this article could be of great assistance.
Unfortunately, SharePoint Online doesn’t allow us to copy pages from one site collection to another. However, we can copy list items and documents. If you want to copy a file or item from a document library to another, select the three dots in front of the item, then select ‘Copy to’ and choose the destination site/library. Since we are unable to do this with pages, I have found a workaround which I will share with you below.
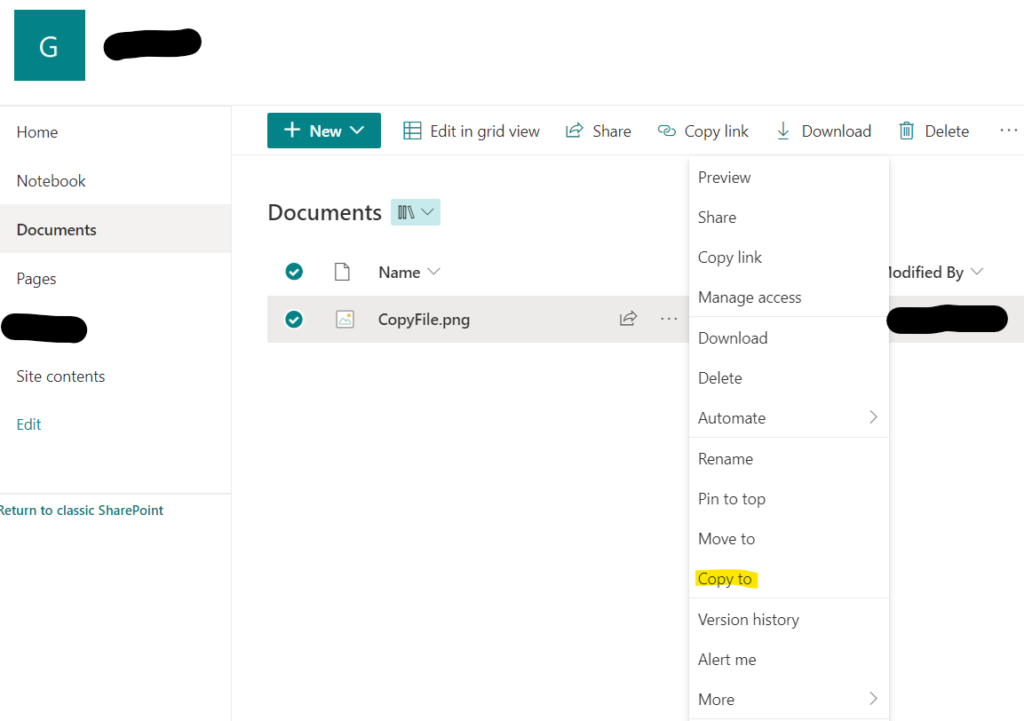
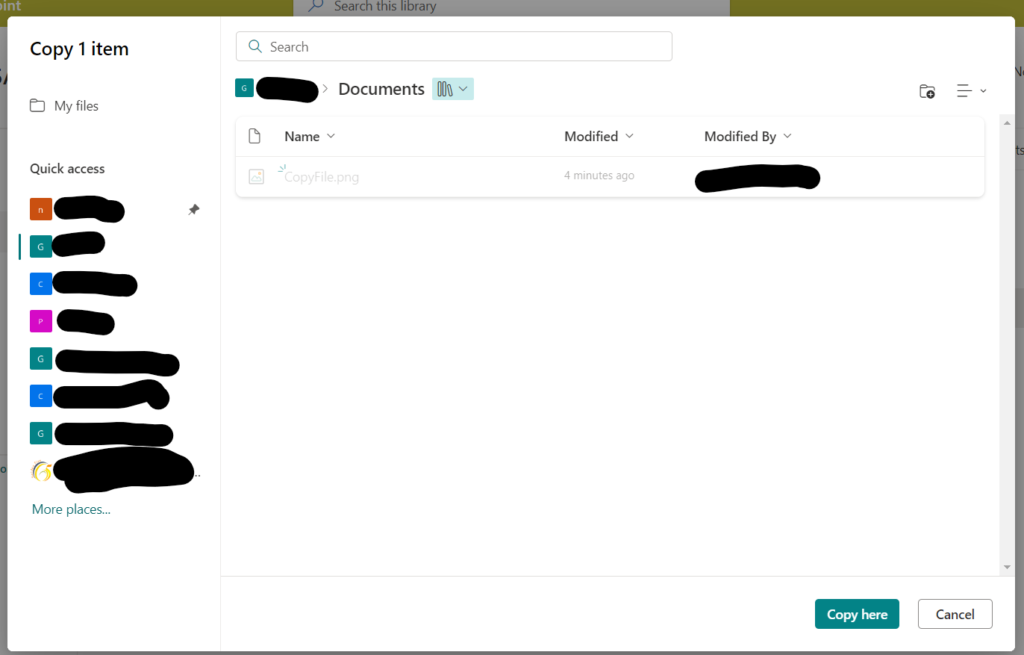
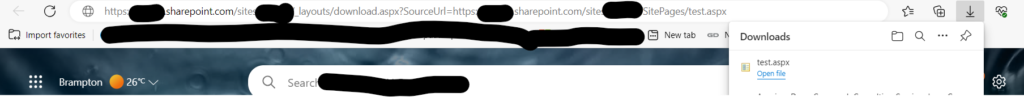
To download a SharePoint page, you can use the following URL format and the file will be downloaded: https://tenant.sharepoint.com/_layouts/download.aspx?SourceUrl=https://tenant.sharepoint.com/SitePages/test.aspx
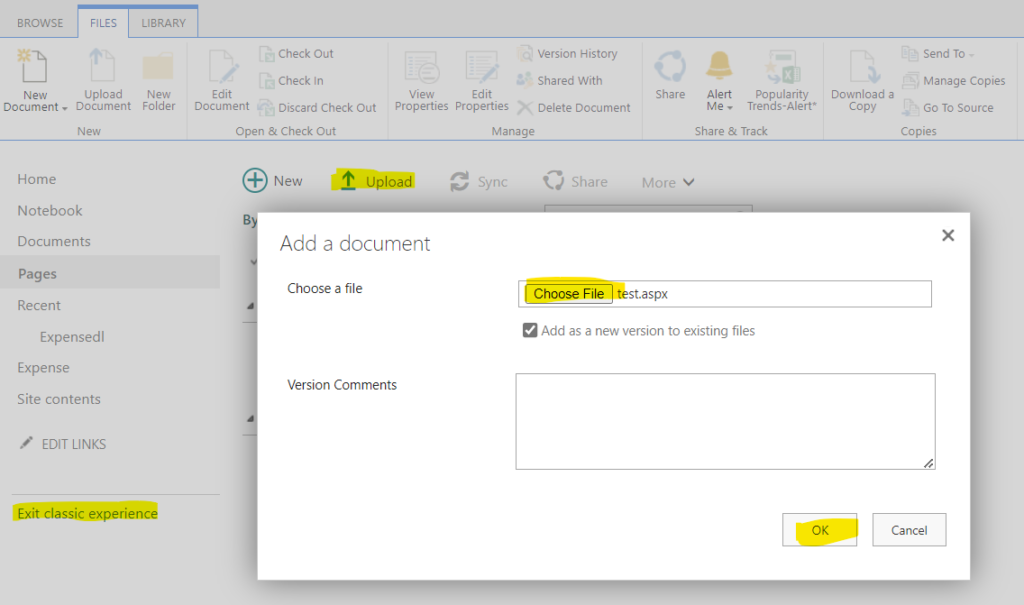
Now you can upload this file to the destination using SharePoint classic view.
Article by: Inderjeet Singh
Cloud Architect
Golden Five Consulting
Using Planner for project and task management
“Stay organized and on track with Planner – the ultimate project and task management tool!”
Introduction
Planner is an indispensable instrument for adept project and task organization. It empowers you to efficiently orchestrate and oversee your endeavors with precision. Its versatile features enable seamless task creation, delegation, deadline establishment, progress monitoring, and team collaboration. Utilizing Planner fosters a streamlined approach, guaranteeing punctual completion and fiscal adherence to your projects. Furthermore, it facilitates meticulous organization, allowing you to prioritize essential aspects effectively.
Integrating Planner into Your Existing Project Management System
Incorporating a planner into an established project management framework offers a strategic avenue for optimizing workflows and elevating overall operational effectiveness. Through harnessing the capabilities of a planner, teams can systematically systematize assignments, monitor advancements, and safeguard punctual completion.
The initial phase of assimilating a planner into an established project management system necessitates the delineation of project aims and objectives. This preliminary step is pivotal in determining the most fitting type of planner for the project at hand. Should the project involve substantial teamwork, a communal workspace-equipped planner may be the most suitable choice. Conversely, if the project entails numerous individual tasks, a planner featuring a task inventory might be more fitting.
Following the identification of the most appropriate planner type, the subsequent step involves devising the integration modality within the existing project management infrastructure. These integration efforts may encompass the establishment of a fresh workspace or seamless fusing of the planner into a preexisting space. It is imperative to ascertain that the planner is in harmony with the current system and facilitates the availability of all essential functions.
Once the planner has been integrated, it is important to ensure that all team members are aware of how to use it. This may involve providing training or creating a user guide. It is also important to ensure that the planner is regularly updated with new tasks and progress.
Finally, it is important to monitor the effectiveness of the planner. This may involve tracking the completion of tasks, the amount of time spent on tasks, and the overall progress of the project. By monitoring the effectiveness of the planner, teams can identify areas for improvement and make adjustments as needed.
Integrating a planner into an existing project management system can be a great way to streamline processes and increase efficiency. By following the steps outlined above, teams can ensure that the planner is properly integrated and used effectively.
How to Use Planner to Track Progress and Monitor Performance
Strategic planning stands as a pivotal cornerstone for the triumph of any enterprise. It orchestrates goal attainment, task completion, and the vigilance of advancement. Leveraging a planner empowers businesses to scrutunize performance and chart progress, facilitating judicious decision-making and goal actualization.
Initiating the use of a planner to monitor performance and track progress demands the establishment of explicit and discernible objectives. This blueprint delineates the enterprise’s trajectory and ensures timely task fulfillment. Following goal delineation, the formulation of a comprehensive timeline assumes paramount importance. This temporal framework incorporates essential milestones and deadlines, serving as navigation beacons for business alignment.
Post timeline delineation, the formulation of a strategy to materialize business objectives becomes imperative. This blueprint embraces requisite tasks, resource allocation, and procedural prerequisites vital for goal realization. Task assignment to designated individuals and the imposition of task-specific deadlines amplify the efficacy of this devised strategy.
Subsequently, the active surveillance of progress and performance ascends to significance. The instantiation of a monitoring system intensifies the enterprise’s capacity to monitor task and goal advancement. This mechanism encompasses task-specific timelines, allocated resources, and salient data fostering comprehensive oversight.
Ultimately, regular scrutiny of the enterprise’s progress and performance asserts its indispensability. This systematic appraisal facilitates the identification of potential areas necessitating refinement and allows for responsive recalibration. Regular performance scrutiny ensures the enterprise’s alignment with its designated trajectory and goal achievement.
Employing a planner to monitor performance and track progress safeguards the enterprise’s trajectory towards goal achievement. Establishment of explicit goals, temporal delineation, and progress assessment guarantee timely task fulfillment and goal realization. Consistent performance reviews empower enterprises to discern areas necessitating refinement and adapt proactively.
Best Practices for Setting Up Your Planner for Project Management
1. Creating a timeline is crucial for effective project management. This timeline must encompass the project’s commencement and conclusion dates, along with key milestones and deadlines to be achieved. It serves as a roadmap, guiding the project towards successful completion.
2. Establish a comprehensive task list to effectively manage the myriad responsibilities entailed in the project. This catalog should encompass task nomenclature, designated task executor, projected time allocation for task completion, and pertinent task interdependencies.
3. Once a definitive timeline and task roster are in place, allocate the requisite resources to each task. This encompasses not only human resources but also the procurement of necessary materials and equipment.
4. Establish a mechanism to meticulously monitor the advancement of each task to ensure the seamless progression of the project. Employing tools like Gantt charts or Kanban boards can facilitate this monitoring endeavor.
5. Vigilantly oversee potential risks that may materialize over the course of the project. This encompasses vigilant monitoring of scope, budget, and timeline alterations, as well as external variables that may precipitate project impact.
6. Foster seamless communication among all involved stakeholders, ensuring that pertinent changes and updates are promptly disseminated to maintain optimal project coherence and efficacy.
By following these best practices, you can ensure that your project is managed effectively and efficiently. With the right planning and organization, you can ensure that your project is completed on time and within budget.
Tips for Maximizing Efficiency with Planner for Task Management
1. Establishing clear goals is vital in maximizing efficiency with a task management planner. This allows for prioritization and better focus on crucial tasks.
2. Fragmenting tasks into smaller, more manageable parts aids in organization and maintaining momentum. It also helps in foreseeing potential obstacles.
3. Employing reminders plays a pivotal role in task management, preventing oversights and bolstering concentration and drive.
4. Task prioritization is pivotal in maximizing efficiency with a task management planner. It avoids feeling swamped and ensures key tasks receive due attention.
5. Monitoring progress is crucial for task upkeep and identifying areas warranting strategy adjustments.
How to Use Planner to Streamline Your Project Management Process
Project management is a complex process that requires careful planning and organization. To ensure that projects are completed on time and within budget, it is important to use a project management tool such as a planner. A planner can help streamline the project management process by providing a clear overview of tasks, deadlines, and resources.
The first step in using a planner to streamline the project management process is to create a timeline. This timeline should include all of the tasks that need to be completed, as well as the deadlines for each task. This timeline should also include any milestones that need to be achieved. Once the timeline is created, it can be used to track progress and ensure that tasks are completed on time.
The next step is to create a task list. This list should include all of the tasks that need to be completed, as well as the resources needed to complete them. This list should also include any dependencies between tasks. For example, if one task needs to be completed before another can begin, this should be noted in the task list.
Once the timeline and task list have been created, it is important to assign tasks to team members. This can be done by assigning tasks to individuals or groups. It is important to ensure that tasks are assigned to the right people, as this will help ensure that tasks are completed on time and within budget.
Finally, it is important to track progress. This can be done by using the timeline and task list to track progress. This will help ensure that tasks are completed on time and within budget.
Using a planner to streamline the project management process can help ensure that projects are completed on time and within budget. By creating a timeline, task list, and tracking progress, project managers can ensure that tasks are completed on time and within budget. This will help ensure that projects are completed successfully and on time.
Conclusion
Leveraging a Planner for project and task administration proves to be a potent method for maintaining order and managing assignments efficiently. This tool empowers users to seamlessly generate tasks, assign them to designated team members, and monitor advancements. It also provides a visual representation of tasks and projects, making it easier to identify areas of improvement and potential bottlenecks. With its intuitive interface and powerful features, Planner is an excellent tool for managing projects and tasks.
