Using Planner for project and task management
“Stay organized and on track with Planner – the ultimate project and task management tool!”
Introduction
Planner is an indispensable instrument for adept project and task organization. It empowers you to efficiently orchestrate and oversee your endeavors with precision. Its versatile features enable seamless task creation, delegation, deadline establishment, progress monitoring, and team collaboration. Utilizing Planner fosters a streamlined approach, guaranteeing punctual completion and fiscal adherence to your projects. Furthermore, it facilitates meticulous organization, allowing you to prioritize essential aspects effectively.
Integrating Planner into Your Existing Project Management System
Incorporating a planner into an established project management framework offers a strategic avenue for optimizing workflows and elevating overall operational effectiveness. Through harnessing the capabilities of a planner, teams can systematically systematize assignments, monitor advancements, and safeguard punctual completion.
The initial phase of assimilating a planner into an established project management system necessitates the delineation of project aims and objectives. This preliminary step is pivotal in determining the most fitting type of planner for the project at hand. Should the project involve substantial teamwork, a communal workspace-equipped planner may be the most suitable choice. Conversely, if the project entails numerous individual tasks, a planner featuring a task inventory might be more fitting.
Following the identification of the most appropriate planner type, the subsequent step involves devising the integration modality within the existing project management infrastructure. These integration efforts may encompass the establishment of a fresh workspace or seamless fusing of the planner into a preexisting space. It is imperative to ascertain that the planner is in harmony with the current system and facilitates the availability of all essential functions.
Once the planner has been integrated, it is important to ensure that all team members are aware of how to use it. This may involve providing training or creating a user guide. It is also important to ensure that the planner is regularly updated with new tasks and progress.
Finally, it is important to monitor the effectiveness of the planner. This may involve tracking the completion of tasks, the amount of time spent on tasks, and the overall progress of the project. By monitoring the effectiveness of the planner, teams can identify areas for improvement and make adjustments as needed.
Integrating a planner into an existing project management system can be a great way to streamline processes and increase efficiency. By following the steps outlined above, teams can ensure that the planner is properly integrated and used effectively.
How to Use Planner to Track Progress and Monitor Performance
Strategic planning stands as a pivotal cornerstone for the triumph of any enterprise. It orchestrates goal attainment, task completion, and the vigilance of advancement. Leveraging a planner empowers businesses to scrutunize performance and chart progress, facilitating judicious decision-making and goal actualization.
Initiating the use of a planner to monitor performance and track progress demands the establishment of explicit and discernible objectives. This blueprint delineates the enterprise’s trajectory and ensures timely task fulfillment. Following goal delineation, the formulation of a comprehensive timeline assumes paramount importance. This temporal framework incorporates essential milestones and deadlines, serving as navigation beacons for business alignment.
Post timeline delineation, the formulation of a strategy to materialize business objectives becomes imperative. This blueprint embraces requisite tasks, resource allocation, and procedural prerequisites vital for goal realization. Task assignment to designated individuals and the imposition of task-specific deadlines amplify the efficacy of this devised strategy.
Subsequently, the active surveillance of progress and performance ascends to significance. The instantiation of a monitoring system intensifies the enterprise’s capacity to monitor task and goal advancement. This mechanism encompasses task-specific timelines, allocated resources, and salient data fostering comprehensive oversight.
Ultimately, regular scrutiny of the enterprise’s progress and performance asserts its indispensability. This systematic appraisal facilitates the identification of potential areas necessitating refinement and allows for responsive recalibration. Regular performance scrutiny ensures the enterprise’s alignment with its designated trajectory and goal achievement.
Employing a planner to monitor performance and track progress safeguards the enterprise’s trajectory towards goal achievement. Establishment of explicit goals, temporal delineation, and progress assessment guarantee timely task fulfillment and goal realization. Consistent performance reviews empower enterprises to discern areas necessitating refinement and adapt proactively.
Best Practices for Setting Up Your Planner for Project Management
1. Creating a timeline is crucial for effective project management. This timeline must encompass the project’s commencement and conclusion dates, along with key milestones and deadlines to be achieved. It serves as a roadmap, guiding the project towards successful completion.
2. Establish a comprehensive task list to effectively manage the myriad responsibilities entailed in the project. This catalog should encompass task nomenclature, designated task executor, projected time allocation for task completion, and pertinent task interdependencies.
3. Once a definitive timeline and task roster are in place, allocate the requisite resources to each task. This encompasses not only human resources but also the procurement of necessary materials and equipment.
4. Establish a mechanism to meticulously monitor the advancement of each task to ensure the seamless progression of the project. Employing tools like Gantt charts or Kanban boards can facilitate this monitoring endeavor.
5. Vigilantly oversee potential risks that may materialize over the course of the project. This encompasses vigilant monitoring of scope, budget, and timeline alterations, as well as external variables that may precipitate project impact.
6. Foster seamless communication among all involved stakeholders, ensuring that pertinent changes and updates are promptly disseminated to maintain optimal project coherence and efficacy.
By following these best practices, you can ensure that your project is managed effectively and efficiently. With the right planning and organization, you can ensure that your project is completed on time and within budget.
Tips for Maximizing Efficiency with Planner for Task Management
1. Establishing clear goals is vital in maximizing efficiency with a task management planner. This allows for prioritization and better focus on crucial tasks.
2. Fragmenting tasks into smaller, more manageable parts aids in organization and maintaining momentum. It also helps in foreseeing potential obstacles.
3. Employing reminders plays a pivotal role in task management, preventing oversights and bolstering concentration and drive.
4. Task prioritization is pivotal in maximizing efficiency with a task management planner. It avoids feeling swamped and ensures key tasks receive due attention.
5. Monitoring progress is crucial for task upkeep and identifying areas warranting strategy adjustments.
How to Use Planner to Streamline Your Project Management Process
Project management is a complex process that requires careful planning and organization. To ensure that projects are completed on time and within budget, it is important to use a project management tool such as a planner. A planner can help streamline the project management process by providing a clear overview of tasks, deadlines, and resources.
The first step in using a planner to streamline the project management process is to create a timeline. This timeline should include all of the tasks that need to be completed, as well as the deadlines for each task. This timeline should also include any milestones that need to be achieved. Once the timeline is created, it can be used to track progress and ensure that tasks are completed on time.
The next step is to create a task list. This list should include all of the tasks that need to be completed, as well as the resources needed to complete them. This list should also include any dependencies between tasks. For example, if one task needs to be completed before another can begin, this should be noted in the task list.
Once the timeline and task list have been created, it is important to assign tasks to team members. This can be done by assigning tasks to individuals or groups. It is important to ensure that tasks are assigned to the right people, as this will help ensure that tasks are completed on time and within budget.
Finally, it is important to track progress. This can be done by using the timeline and task list to track progress. This will help ensure that tasks are completed on time and within budget.
Using a planner to streamline the project management process can help ensure that projects are completed on time and within budget. By creating a timeline, task list, and tracking progress, project managers can ensure that tasks are completed on time and within budget. This will help ensure that projects are completed successfully and on time.
Conclusion
Leveraging a Planner for project and task administration proves to be a potent method for maintaining order and managing assignments efficiently. This tool empowers users to seamlessly generate tasks, assign them to designated team members, and monitor advancements. It also provides a visual representation of tasks and projects, making it easier to identify areas of improvement and potential bottlenecks. With its intuitive interface and powerful features, Planner is an excellent tool for managing projects and tasks.
Managing user accounts and licenses in Office 365
“Manage user accounts and licenses in Office 365 with ease!”
Introduction
Office 365, a potent cloud-based platform, offers an array of tools and services for businesses to effectively oversee their user accounts and licenses. The management of these accounts and licenses within Office 365 can prove to be intricate, yet it is imperative for businesses to guarantee appropriate access to services and applications for their users. This guide will furnish an outline of the diverse user account and license management options accessible in Office 365, along with optimal strategies for overseeing user accounts and licenses in this environment.
How to Secure User Accounts and Licenses in Office 365
Office 365, a robust suite of cloud-based applications, possesses the capacity to enhance productivity and foster collaboration within businesses of varying scales. However, the ascent of cloud-based services necessitates the establishment of fortified safeguards to uphold the integrity of user accounts and licenses. This discourse aims to furnish an overview of prudent measures to fortify user accounts and licenses within the realm of Office 365.
One pivotal strategy entails the implementation of Multi-Factor Authentication (MFA). This security protocol mandates users to furnish two or more forms of validation to substantiate their identity. Such forms may encompass something known solely to the user (e.g., a password), possession of an item (e.g., a phone or security token), or biological attributes (e.g., fingerprint or facial recognition). The adoption of MFA fortifies user accounts against illicit access and is advised for universal integration across Office 365 user base.
Vigilant monitoring of user activity within the periphery of Office 365 assumes paramount significance. This surveillance is imperative to forestall instances where users inappropriately access or disseminate sensitive information. Utilization of Office 365 tools, notably the Office 365 Security & Compliance Center, facilitates diligent monitoring, unravelling any anomalous user conduct.
Effective license management within the domain of Office 365 is indispensable to ascertain that users exclusively procure essential applications and services. Pruning redundant licenses thwarts unauthorized access and contributes to cost mitigation.
Employing Data Loss Prevention (DLP) policies represents an instrumental shield against unauthorized disclosure or retrieval of sensitive data. These policies can be meticulously configured to identify and interdict the transmission of confidential information, encompassing entities such as credit card numbers, social security numbers, and other classified data.
By following these steps, businesses can ensure that user accounts and licenses in Office 365 are secure. Implementing these security measures can help protect user accounts from unauthorized access and ensure that sensitive information is not shared without authorization.
How to Troubleshoot Common Issues with User Accounts and Licenses in Office 365
Microsoft Office 365, a robust suite of productivity tools, offers businesses the opportunity to enhance efficiency and collaboration at every scale. Nevertheless, the management of user accounts and licenses can present formidable challenges. In this discourse, we will delve into the resolution of prevalent issues concerning user accounts and licenses within Office 365.
1. User Account Predicaments
When a user encounters difficulties in accessing their Office 365 account, the initial course of action involves validating the user’s credentials. It is imperative to ascertain the accuracy of the username and password, while also ensuring that the user has not surpassed the maximum threshold for unsuccessful login attempts. Should the credentials prove accurate, the user might necessitate a password reset.
In the event that the user continues to encounter impediments in gaining access, the root cause may stem from a discrepancy in their Office 365 license. It becomes essential to verify the user’s license status to guarantee its active standing and that the user possesses the requisite permissions. In cases where the license appears inactive, it is advisable to engage the Office 365 administrator for reactivation.
2. License Conundrums
Difficulties in accessing specific functionalities within Office 365 could stem from issues surrounding a user’s license. It is crucial to substantiate the active status of the user’s license and the appropriateness of their permissions. Upon identifying an inactive license, it is prudent to enlist the assistance of the Office 365 administrator to effectuate reactivation.
Should the user possess the appropriate license yet remain incapable of accessing certain functionalities, the underlying issue might pertain to their permissions. A meticulous review of the user’s permissions is imperative to ascertain the appropriateness of their access levels. In instances where erroneous permissions are discerned, it is recommended to liaise with the Office 365 administrator for necessary adjustments.
3. Troubleshooting Strategies
Should the challenges in troubleshooting user accounts and licenses persist, several strategies can be instrumental. Firstly, ensuring the utilization of the latest Office 365 version is paramount. Secondly, validating the accuracy of user credentials and license status assumes significance. Thirdly, meticulous scrutiny of user permissions to verify the appropriateness of their access levels is imperative. Ultimately, seeking guidance from the Office 365 administrator becomes indispensable if obstacles persist.
Adhering to these prescribed measures should facilitate the resolution of prevalent user account and license issues within Office 365. Should challenges persist, seeking the guidance of the Office 365 administrator is advised.
How to Automate User Account and License Management in Office 365
Office 365, a robust cloud-based platform, offers diverse tools and services for efficient collaboration. Nonetheless, the arduous task of managing user accounts and licenses demands considerable time and effort. Fortunately, there exist multiple methods to automate these processes within Office 365.
The initial step involves establishing a centralized repository for user accounts, achievable through the utilization of the Azure Active Directory (AD) service. This enables the creation of a singular, authoritative source for all user accounts, simplifying management across various Office 365 tenants.
Once the central repository is in place, utilizing the Office 365 Admin Center facilitates swift and seamless user account and license management. This comprehensive toolset empowers administrators to expediently create new user accounts, allocate licenses, and regulate user access to Office 365 services.
Employing PowerShell scripts provides another avenue for automating user account and license management. These scripts afford rapid and efficient user account creation, license allocation, and access management within Office 365 services.
Furthermore, leveraging third-party tools offers additional capabilities for automating user account and license management. Diverse third-party solutions deliver an array of features to streamline user account and license management, ensuring efficient and secure management within Office 365.
By implementing automation for user account and license management in Office 365, significant time and effort savings can be realized, while also ensuring the efficient and secure management of user accounts and licenses.
Best Practices for Managing User Accounts and Licenses in Office 365
1. A robust naming protocol for user accounts is crucial in handling Office 365 user accounts and licenses. This aids in easy identification of user accounts and accurate assignment of licenses.
Automation tools are essential for simplifying the intricate task of managing user accounts and licenses within Office 365. These tools enable the creation of user accounts, allocation of licenses, and the regulation of user access.
Monitoring user activity is a fundamental aspect of overseeing user accounts and licenses within Office 365. It aids in the identification of inactive users and safeguards against the wastage of licenses.
The implementation of Role-Based Access Control (RBAC) is a potent strategy for governing user accounts and licenses in Office 365. It facilitates the assignment of precise permissions to users according to their organizational roles.
Employing Multi-Factor Authentication (MFA) is crucial for securing user accounts and licenses within Office 365. MFA fortifies user accounts against unauthorized entry and ensures that only authorized personnel can access sensitive data.
Harnessing Group-Based Licensing is an invaluable asset for managing user accounts and licenses in Office 365. This approach allows for the assignment of licenses to user groups, thus minimizing the quantity of licenses required for individual allocation.
Vigilant monitoring of license usage is imperative for effective management of user accounts and licenses in Office 365. It serves to pinpoint dormant licenses and guarantees their optimal utilization.
Employing Self-Service Password Reset (SSPR) is a beneficial tool for administering user accounts and licenses in Office 365. It enables users to independently reset their passwords, alleviating the demand for IT support.
Delegated administration is a formidable tool for overseeing user accounts and licenses in Office 365. It empowers the allocation of specific administrative responsibilities to users, enabling IT personnel to focus on more critical duties.
10. Utilize Security Groups: Security groups are an important tool for managing user accounts and licenses in Office 365. Security groups can be used to assign permissions to users and ensure that only authorized users have access to sensitive data.
How to Manage User Accounts and Licenses in Office 365
Office 365 offers a robust cloud-based platform packed with diverse applications and services. Administering user accounts and licenses in Office 365 is crucial for efficient management. Delving into the nuances of handling user accounts and licenses in Office 365 is the focus of this write-up.
To initiate the process, creation of user accounts takes precedence. This can be accomplished via the Office 365 Admin Center, serving as a hub for adding new users, license allocation, and management of existing user accounts. Additionally, user roles, permissions, and settings can be configured in this portal.
Once the user accounts are in place, the subsequent task involves license assignment. This pivotal task can be executed through the Office 365 Admin Center. It entails selecting the pertinent license type and assigning it to the specific user or group.
Further, delving into user settings administration is crucial. This control resides within the Office 365 Admin Center, allowing for the fine-tuning of settings such as password policies, access control, and security measures. Moreover, customization of language, time zone, and regional settings is possible.
Lastly, vigilant monitoring of user activity and usage through the Office 365 Admin Center is vital. This involves scrutinizing usage reports and tracking user actions to preempt potential security loopholes and drawbacks.
Following these steps diligently will effectively encompass the management of user accounts and licenses in Office 365. This not only ensures streamlined access to requisite applications and services for users but also bolsters the organizational shield against potential security vulnerabilities.
Conclusion
Effectively administering user accounts and licenses in Office 365 is essential for optimizing organizational efficiency and security. By adeptly handling user accounts, allocating licenses, and regulating access to Office 365 services, you can streamline operations and fortify data protection. By implementing appropriate tools and procedures, your organization can harness the myriad features and advantages offered by Office 365.
How to get rid of error ‘The email address is already being used. Please choose another email address’
Today, I had mistakenly created a user account instead of shared mailbox so I wanted to delete and recreate it as a shared mailbox but kept getting error ‘The email address is already being used. Please choose another email address.’
After some research I found that if we want to use the same email address as an alias of our primary account, we have to wait for 30 days prior to the date when deleted. But we have an alternate workaround for same, we can hard delete the email address using below command.
Remove-Mailbox -Identity <Identity> -Permanent $true
So, I opened PowerShell from top right navigation as shown below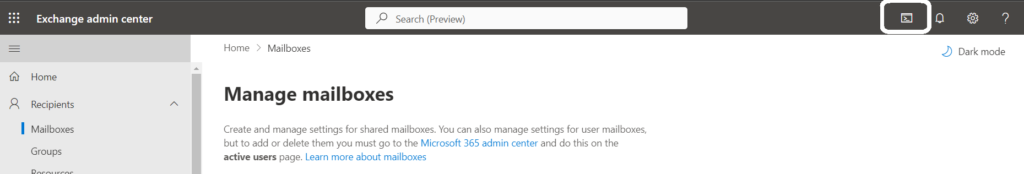
If you are running it for the 1st time, it will create a new database to log the powershell command and its output. as shown below
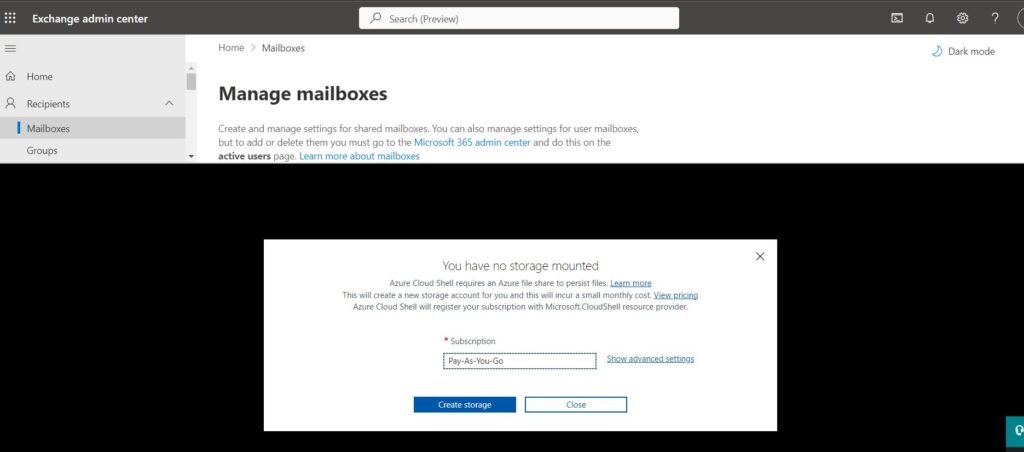
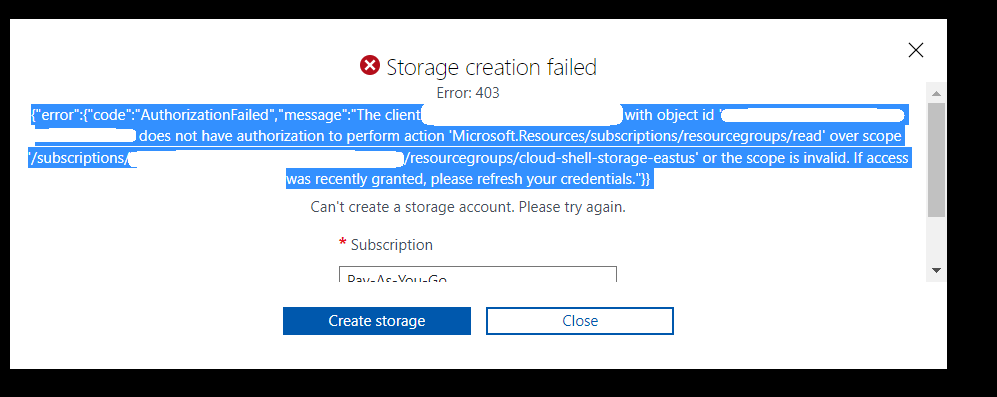
If you don’t have at least contribute access on subscription, you will get error ‘{“error”:{“code”:”AuthorizationFailed”,”message”:”The client ‘UserID’ with object id ‘xxx’ does not have authorization to perform action ‘Microsoft.Resources/subscriptions/resourcegroups/read’ over scope ‘/subscriptions/subscriptionnumber/resourcegroups/cloud-shell-storage-eastus’ or the scope is invalid. If access was recently granted, please refresh your credentials.”}}
Note : Microsoft is updating few policies so few command including this one may not work for all tenants so use the alternate method mentioned below
Or
You can even run PowerShell from your local machine as shown below:
Now you can use below command and remove the mailbox, now you should be able to create the Shared mailbox without any error.
Remove-Mailbox -Identity <Identity> -PermanentDelete $true
Article from:
Inderjeet Singh Jaggi
Published a user\shared mailbox calendar and add it to SharePoint page or even with someone outside the organization
1. Make sure you have send-as permission on the mailbox from Admin center.
2. Sign-in to Outlook web app (https://outlook.office365.com/owa) with your Office 365 account or open mailbox.
3. If its shared mailbox click on your name on top right corner of the screen and then select Open other users mailbox, type shared mailbox details.
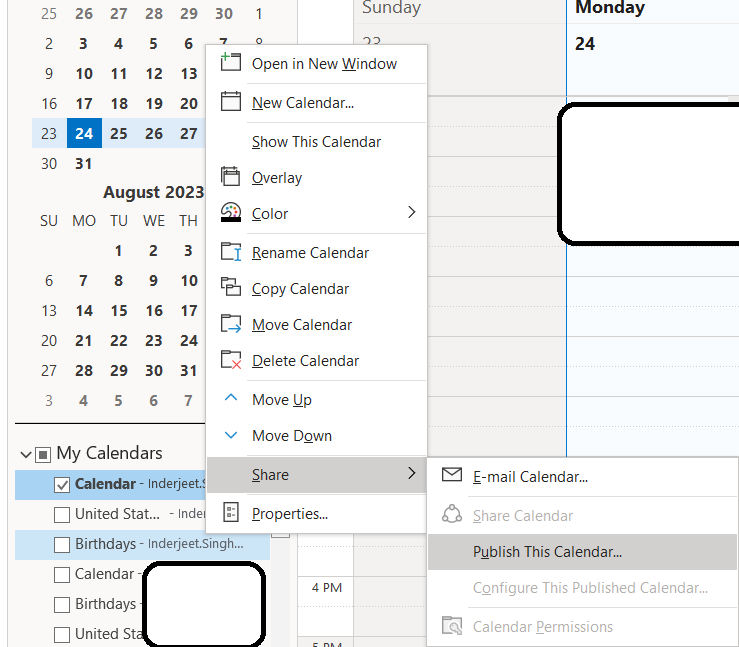
4. Navigate to the calendar and right-click the calendar you want to share. Select Share > Publish this calendar > Share this calendar as shown below:
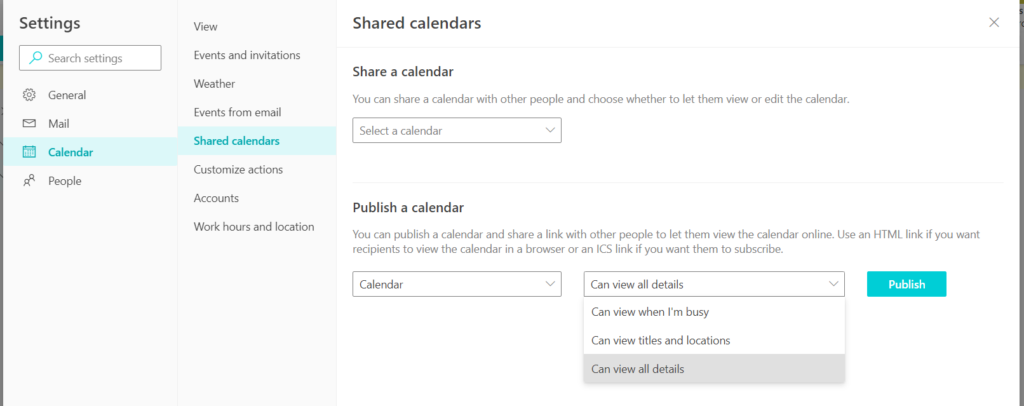
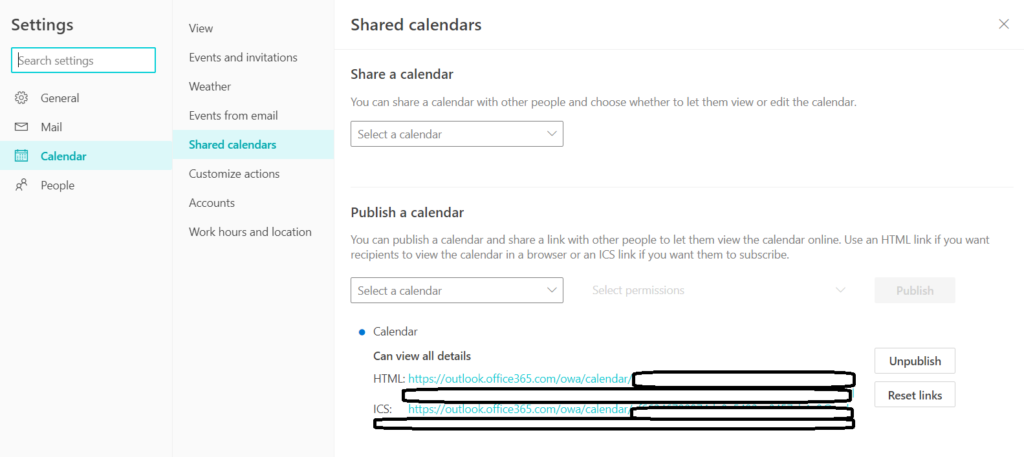
5. Now select Can view all details or any other option and select Publish
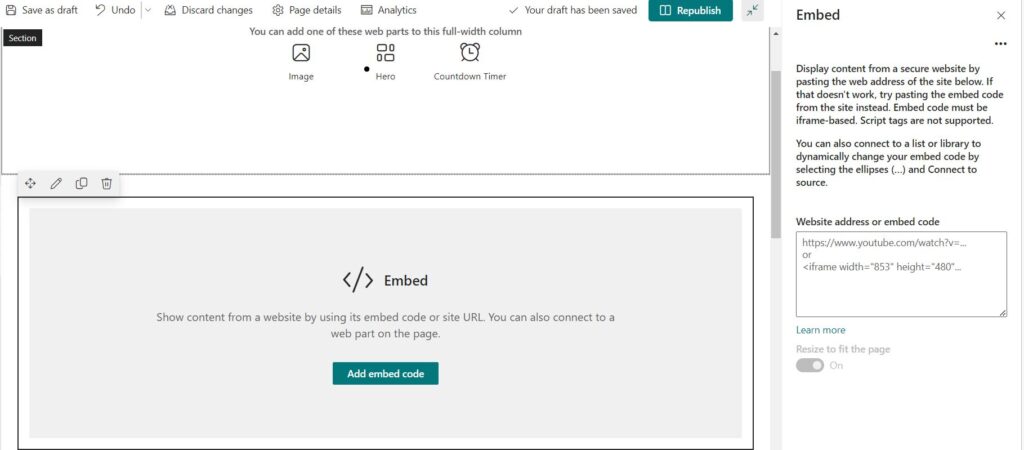
Now open the SharePoint page and add a script editor app. Add below code to the app. I have hidden the GUID in above screenshot.
<iframe src=”https://outlook.office365.com/owa/calendar/SOMEGUID/calendar.html” height=”400px” width=”400px”></iframe>

Article from:
Inderjeet Singh Jaggi
Connecting Office 365 to other applications and services using APIs and connectors
“Unlock the Power of Office 365: Connect to Any Application or Service with APIs and Connectors!”
Introduction
Integrating Office 365 with external applications and services through APIs and connectors presents a compelling avenue to amplify its functionalities and streamline interoperability. By leveraging these tools, users gain access to external data, enabling its seamless utilization within the Office 365 ecosystem. This convergence facilitates the automation of tasks, the creation of tailored workflows, and more. By selecting appropriate APIs and connectors, seamless integration with external platforms becomes achievable, unlocking the full potential of Office 365.
How to Troubleshoot Common Issues When Connecting Office 365 to Other Services Using APIs and Connectors
Integrating Office 365 with other services via APIs and connectors offers a promising avenue for optimizing workflows and bolstering efficiency. Nonetheless, this process is often intricate and susceptible to mishaps. Accordingly, we shall explore prevalent complications stemming from the interconnection of Office 365 and external services, alongside strategies for resolving these issues.
Foremost among these challenges are authentication hitches, which frequently stem from inaccuracies in user credentials, expired access tokens, or inadequate permissions. Addressing this demands diligence in validating the correctness of credentials and ensuring the currency of access tokens, alongside verifying the user’s entitlement to requisite permissions.
Subsequently, connection glitches may manifest as a consequence of faltering links between Office 365 and associated services. This could result from suboptimal or unstable network connectivity, or the obstruction posed by firewalls. Mitigating such woes necessitates vigilance in upholding the stability of the connection and ensuring that firewalls do not impede the linkage.
Furthermore, discrepancies in data synchronization may impede the seamless operation between Office 365 and other services. These discrepancies can arise from misconfigured settings or inadequacies in data synchronization procedures. Addressing this entails meticulous scrutiny of settings and confirming the fidelity of data synchronization mechanisms.
Concurrently, complications in API functionality could disrupt the harmonious synergy between Office 365 and external services. These could arise from erroneous configurations or deficiencies in API support. Tackling this quandary mandates meticulous verification of the accuracy of settings and ascertaining the compatibility of the API in use.
By following these steps, you should be able to troubleshoot most common issues when connecting Office 365 to other services using APIs and connectors. If you are still having issues, it is recommended that you contact the service provider for further assistance.
Best Practices for Securing Connections Between Office 365 and Third-Party Applications
When establishing connections between Office 365 and third-party applications, prioritizing secure configurations is paramount, especially when handling sensitive data like customer information or financial records. Implementing best practices for securing these connections is crucial:
Firstly, employing Multi-Factor Authentication (MFA) is essential. MFA adds an extra layer of security by necessitating multiple forms of verification, such as passwords, mobile device verification codes, or biometric authentication, to validate user identity, thereby mitigating unauthorized access.
Secondly, leveraging encryption is imperative. Encrypting data is vital to rendering it indecipherable to unauthorized parties. Ensuring that encryption is in place when bridging Office 365 with third-party applications safeguards sensitive information from potential breaches.
Vigilant Oversight of Data Access: Maintaining a keen eye on the individuals who have the privilege of accessing sensitive information is paramount. This can be achieved by closely monitoring user actions through audit logs and implementing proactive alerts to promptly notify administrators of any potentially suspicious behavior.
Adhere to Robust Security Protocols: When establishing connections between Office 365 and external applications, it is imperative to employ stringent security protocols such as HTTPS or SFTP. These protocols play a pivotal role in guaranteeing end-to-end encryption, thereby safeguarding data from unauthorized access or unauthorized modification.
Harness the Power of VPN: Leveraging a virtual private network (VPN) for the linkage between Office 365 and third-party applications is essential to fortify data security. By utilizing a VPN, the integrity of data is preserved through encryption, mitigating the risks posed by potential interception or unauthorized alteration.
By following these best practices, organizations can ensure that their connections between Office 365 and third-party applications are secure. This will help to protect sensitive data and ensure that only authorized users have access to it.
An Overview of the Different Types of Connectors Available for Connecting Office 365 to Other Applications
Featuring a plethora of cloud-based tools and services, Office 365 stands as an influential productivity suite promoting effective collaboration and enhanced work efficacy. Maximizing the potential of this platform necessitates seamless integration with diverse applications and services, facilitated by a myriad of available connectors.
Among these, the widely prevalent Office 365 Outlook connector takes precedence. Empowering users to interlink their Outlook account with various applications like Salesforce, Dropbox, and Google Drive, this feature facilitates unified access to emails, contacts, and calendar across platforms.
Equally prominent is the Office 365 OneDrive connector, enabling users to synchronize their OneDrive account with applications such as Dropbox, Box, and Google Drive, thereby enabling streamlined accessibility to files across different interfaces.
Furthermore, the Office 365 SharePoint connector emerges as a valuable asset, allowing users to amalgamate their SharePoint site with applications like Salesforce, Dropbox, and Google Drive, ensuring unified access to documents, lists, and diverse content.
Notably, the Office 365 Power BI connector holds significance, enabling users to interlink their Power BI account with applications such as Salesforce, Dropbox, and Google Drive, thereby facilitating embedded access to data and analytics.
Lastly, the Office 365 Flow connector stands as a pivotal asset, empowering users to connect their Flow account with various applications like Salesforce, Dropbox, and Google Drive, thereby enhancing workflow integration. This allows users to automate tasks and processes from within the other applications.
These are just a few of the connectors available for connecting Office 365 to other applications. There are many more connectors available, and they can be used to connect Office 365 to a wide variety of applications and services. By taking advantage of these connectors, users can make the most of Office 365 and get the most out of their productivity suite.
Exploring the Benefits of Connecting Office 365 to Other Services Using Connectors
Integrating Office 365 with various services through connectors offers an effective means to streamline operations and enhance effectiveness. By linking Office 365 with services like Twitter, Salesforce, and Dropbox, users can seamlessly access external data from within the Office 365 environment, simplifying information retrieval and facilitating collaborative endeavors.
The connectors not only establish a secure conduit to bridge Office 365 and other platforms, but also streamline access to data without necessitating multiple logins. Consequently, the cumbersome task of toggling between different applications is alleviated, saving valuable time and resources. Furthermore, these connectors can be employed to automate specific functions, such as triggering notifications or generating tasks in Office 365 based on events in external services.
Facilitating collaboration is another noteworthy facet of connectors. For instance, users can effortlessly distribute documents from Dropbox or Salesforce to colleagues in Office 365, eliminating the need for manual uploads. Moreover, swift access to client information from platforms like Salesforce or Twitter directly within Office 365 equips users to promptly address customer queries, enhancing operational efficiency.
The integration of Office 365 with external services via connectors presents a potent instrument for optimizing workflows and bolstering productivity. These connectors forge robust connections between Office 365 and external platforms, streamlining data accessibility and obviating the need for multiple login credentials. The seamlessness of this integration also catalyzes smooth collaboration with colleagues and clients, alongside the automation of tailored workflows to augment agility in adaptation to evolving dynamics.
How to Connect Office 365 to Third-Party Applications Using APIs
Linking Office 365 with third-party apps via APIs expands Office 365’s capabilities and streamlines integration with diverse applications. APIs enable developers to tap into Office 365’s data and services for use in their own applications.
To establish the connection between Office 365 and third-party apps, leveraging the Office 365 APIs is essential. These APIs furnish access to a broad array of Office 365 data and services, encompassing Outlook, OneDrive, SharePoint, and beyond. They empower developers to craft tailor-made applications that mesh with Office 365 or extract data for utilization in their own apps.
Initiating the linkage between Office 365 and third-party apps involves registering the app with the Office 365 API. This entails furnishing pertinent details including the app’s moniker, a brief overview, and a redirect URL. Subsequently, post-registration, a Client ID and Client Secret are issued for utilization in API invocations.
Following successful registration, endeavors to interact with Office 365 via API calls commence. These API calls facilitate extraction of diverse data from Office 365, spanning user details, calendar entries, and beyond. Furthermore, they offer the capability to formulate bespoke applications that harmonize with Office 365, such as custom CRM systems or tailored document management solutions.
Employing APIs to interface Office 365 with third-party apps imparts a means to augment Office 365’s functionality and facilitate seamless integration with other applications. With adept API usage, one can create custom applications that dovetail with Office 365 and tap into Office 365’s data within their own applications.
Conclusion
Linking Office 365 with other apps and services through APIs and connectors is an effective means to amplify Office 365’s functionalities and streamline its integration with diverse systems. This enables users to retrieve data from various origins, automate operations, and forge tailored solutions. Armed with suitable APIs and connectors, Office 365 becomes a platform for crafting potent applications and services, thus propelling businesses towards heightened efficacy and productivity.
How to access PowerBI anonymous site using SharePoint 2013 (Authenticated) without exposing the anonymous URL
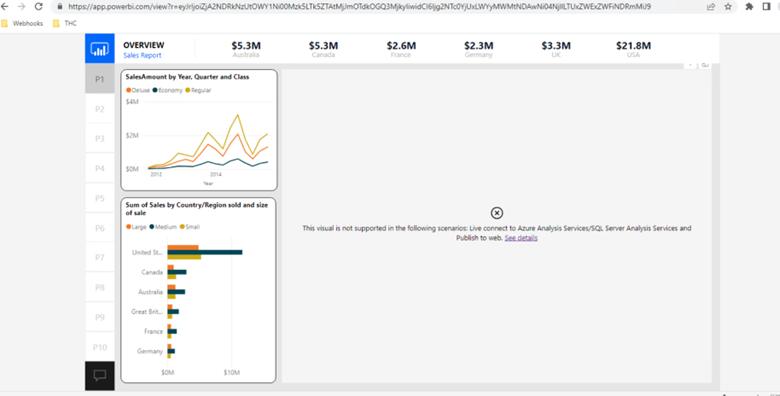
Publish the PowerBI site for anonymous user and try to browse the PowerBI dashboard on the SharePoint site make sure it is working fine
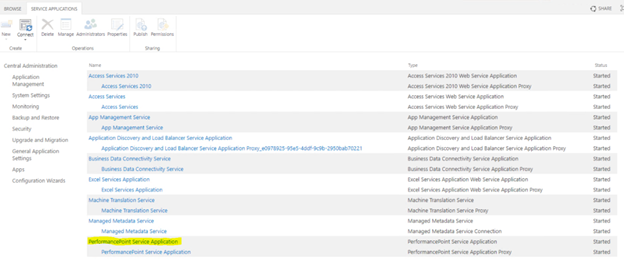
Configure Performance Point Service Application. To do so follow below article.
Configure PerformancePoint Services – SharePoint Server | Microsoft Learn
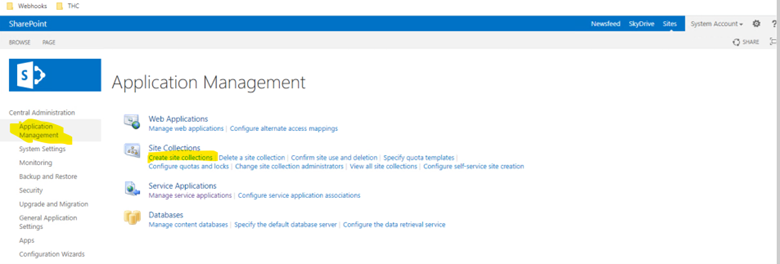
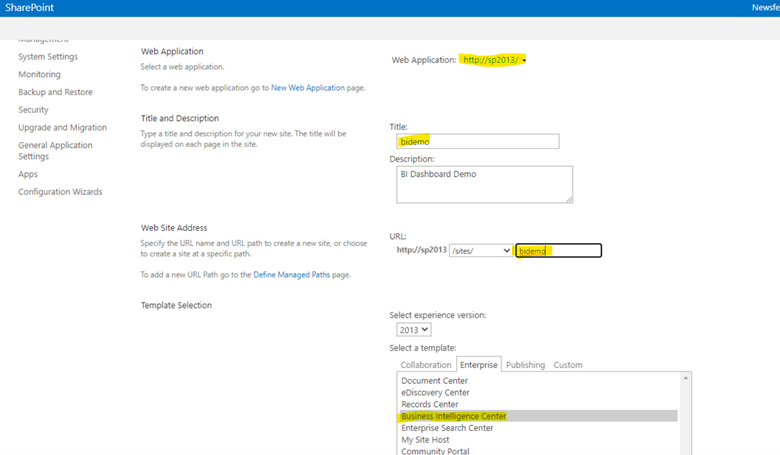
Now create a new site collection . To do so, Click Application Management > Create Site collections > Select appropriate web application > Provide details such as title, url, admin > Make sure the site collection template is named as ‘Business Intelligence Center’ under Enterprise tab. > Click OK
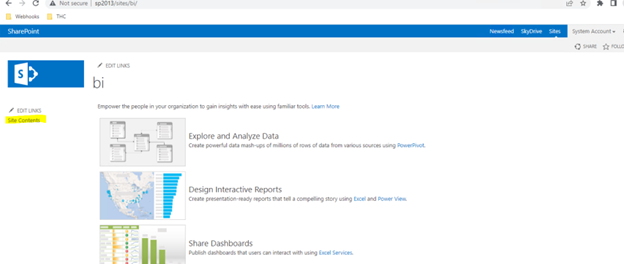
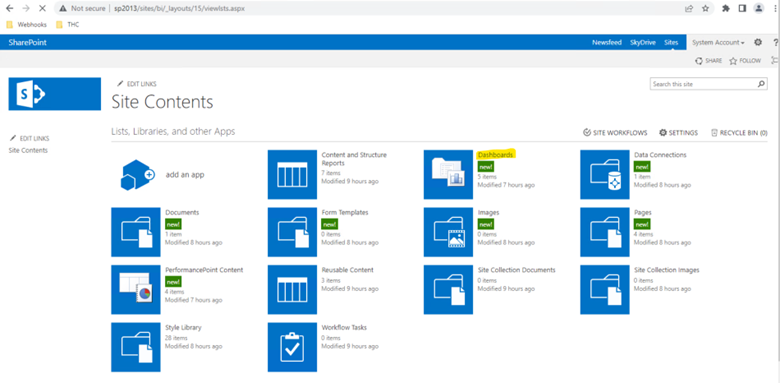
Once Site collection is ready, Browse the site > select site content > select Dashboard
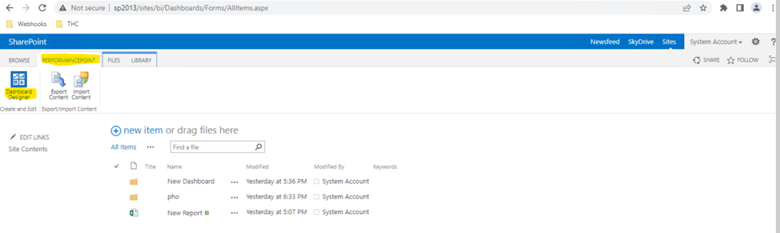
Select PerformancePoint on top and then select ‘Dashboard Designer’ > It will download and open Dashboard Designer application on the screen(If IE doesn’t work try Chrome browser)
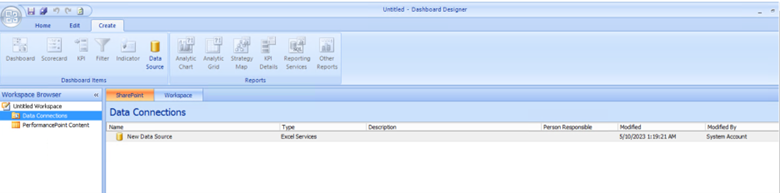
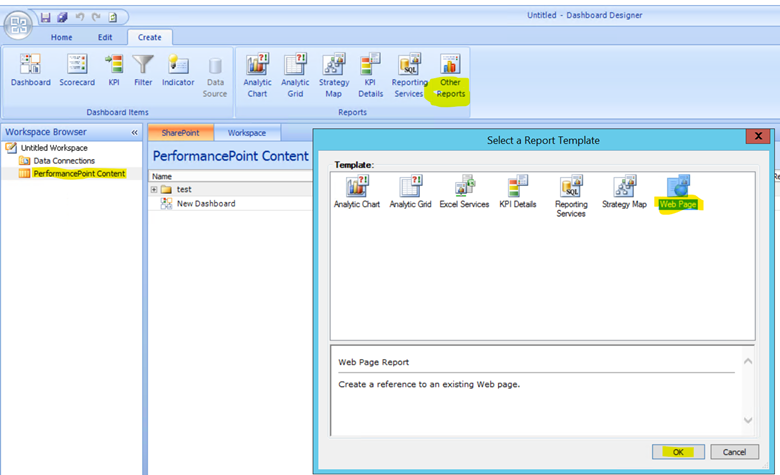
Select ‘PerformancePoint Content’ > Other Reports > Web Page > Click OK
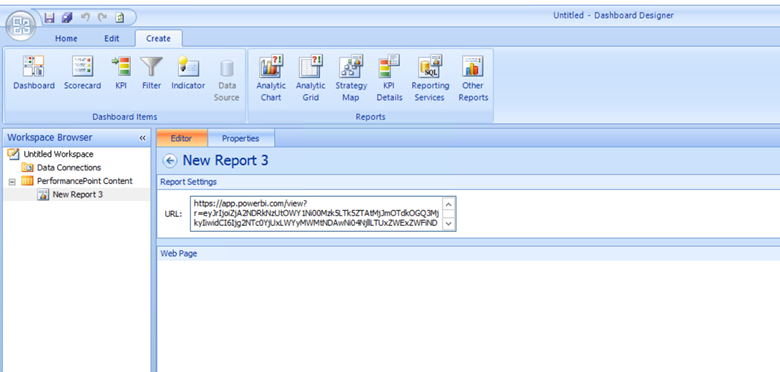
Enter the PowerBI URL in the URL. Also you can rename the name of report from left navigation to something easy.
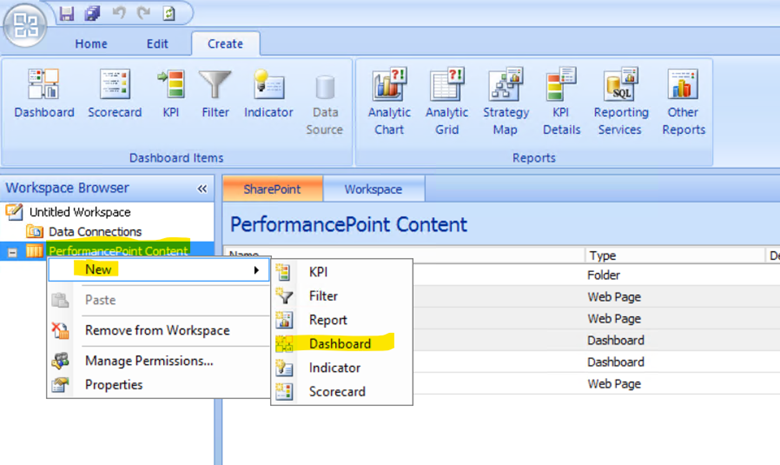
Right click ‘PerformancePoint Content’ > New > Dashboard
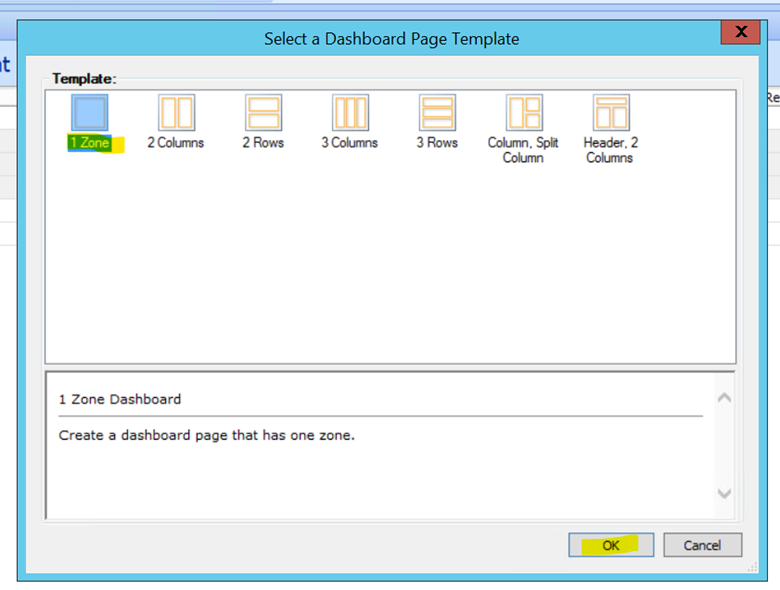
Select 1 zone from template and click OK
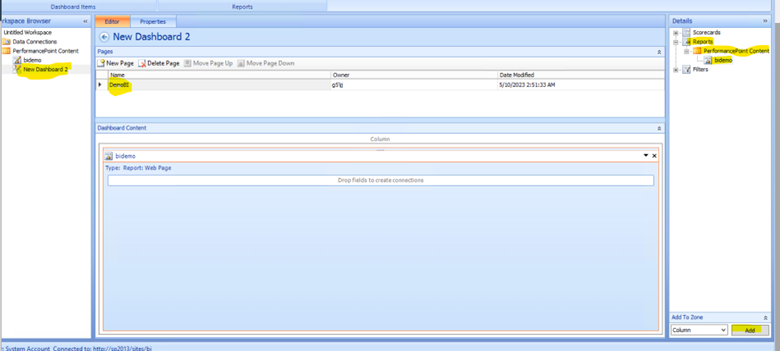
Now Rename the Dashboard from left navigation > Name the page to something easy to understand > From right hand navigation expand Reports > PerformancePoint Content > BIdemo > Click Add at bottom of screen
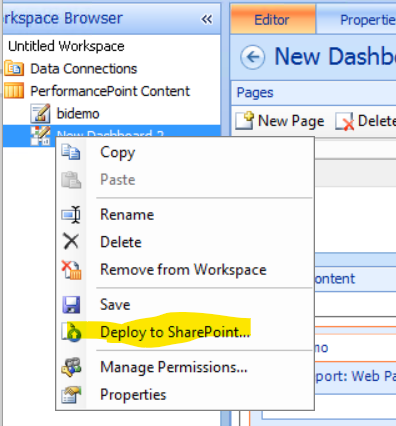
Now right click on Dashboard and select ‘Deploy to SharePoint’
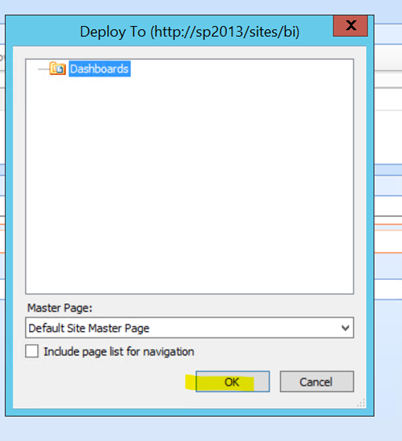
Click OK
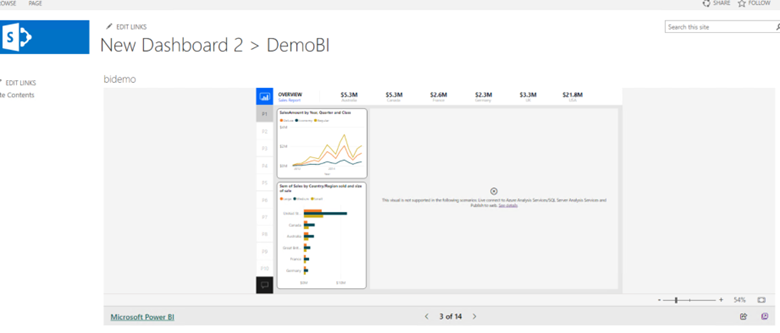
Once published, you will be routed the page which has the new Dashboard published with PowerBI running in the background
Here when checked the source on the page, we wouldn’t be able to find the path of the anonymous site published in PowerBI
Access to this SharePoint page can managed using SharePoint permissions
Article from:
Inderjeet Singh Jaggi
Cloud Architect – Golden Five Consulting
Using Office 365 to communicate and collaborate with external partners and clients
“Connect with the world: Office 365 for seamless communication and collaboration with external partners and clients.”
Introduction
Office 365 serves as a robust instrument for enterprises to foster communication and cooperation with external associates and clientele. This dynamic tool furnishes a secure stage for sharing pertinent documents, orchestrating meetings, and engaging in joint endeavors. Leveraging Office 365 empowers businesses to effortlessly keep external associates and clients abreast of project advancements, share documents, and engage in real-time interaction. Moreover, the platform furnishes a secure enclave for enterprises to store and dispense sensitive information to their external partners and clients, thereby facilitating adherence to industry regulations and safeguarding data integrity. This discourse will expound upon the advantages of harnessing Office 365 for interfacing and collaborating with external partners and clients.
Best Practices for Using Office 365 to Communicate and Collaborate with External Partners and Clients
1. Formulate Comprehensive Communication Standards: Establishing unambiguous communication guidelines is paramount for fostering effective collaboration with external associates and clientele. This encompasses defining anticipated response times, preferred modes of communication, and the nature of information to be exchanged.
2. Employ Office 365’s Robust Security Features: Office 365 provides an array of security measures that fortify data integrity and restrict access solely to authorized personnel. These encompass multifaceted authentication, data loss prevention, and encryption protocols.
3. Harness the Potential of Office 365 Groups: Office 365 Groups serve as an exceptional avenue for cooperative endeavors with external partners and clients. They facilitate seamless document sharing, task delegation, and inter-member communication.
4. Embrace Office 365 Video Capabilities: Office 365 Video serves as an efficacious conduit for engaging external partners and clients. Video functionality allows for facile dissemination of presentations, training materials, and other pertinent content.
5. Make Use of Office 365 Planner: Office 365 Planner stands as a commendable instrument for overseeing joint ventures with external partners and clients. It enables effortless task assignment, progress monitoring, and collaboration.
6. Exploit the Advantages of Office 365 Yammer: Yammer provides a valuable avenue for interacting with external partners and clients. It affords seamless sharing of ideas, inquiry facilitation, and collaboration.
7. Employ Office 365 Delve for Insight: Delve is an invaluable resource for discovering content shared by external partners and clients. It facilitates easy retrieval of documents, discussions, and other shared material.
8. Harness the Potential of Office 365 Skype for Business: Skype for Business presents a robust platform for interaction with external partners and clients. Skype for Business allows you to easily make audio and video calls, share screens, and collaborate with your partners and clients.
9. Utilize Office 365 Sway: Sway is a great way to create interactive presentations and share them with external partners and clients. Sway allows you to easily create presentations that are engaging and interactive.
10. Take Advantage of Office 365 Forms: Office 365 Forms is a great way to collect feedback from external partners and clients. Forms allows you to easily create surveys and polls and collect feedback from your partners and clients.
Exploring the Benefits of Office 365 for External Partners and Clients
Office 365, a robust suite of cloud-based applications, enhances productivity, collaboration, and communication for businesses of all scales. External partners and clients reap assorted advantages from Office 365, empowering them to operate with enhanced efficiency and efficacy.
A pivotal benefit for external partners and clients lies in the ubiquitous access to their documents and data. Office 365 enables users to retrieve their information from any internet-connected device, facilitating seamless collaboration, document sharing, and access to vital details.
Moreover, Office 365 encompasses an array of collaboration tools conducive to enhanced teamwork among external partners and clients. Notably, Microsoft Teams facilitates real-time project collaboration through chat, file sharing, and collective work. Additionally, Office 365 offers other collaborative resources such as SharePoint for document creation and sharing, and OneDrive for file storage and sharing.
Furthermore, Office 365 boasts a suite of security features aimed at safeguarding the data of external partners and clients. These encompass multi-factor authentication, mandating additional authentication factors for data access, and data encryption to fortify data against unauthorized breaches.
Lastly, Office 365 furnishes an assortment of analytics tools, empowering external partners and clients to extract valuable insights from their data. Notably, Power BI enables the creation of interactive data visualizations, while Excel facilitates robust data analysis and manipulation.
In summary, Office 365 presents a myriad of advantages for external partners and clients. From ubiquitous data access to multifaceted collaboration and security features, Office 365 serves to enhance the efficacy and efficiency of external partners and clients.
Utilizing Office 365 to Improve Communication with External Partners and Clients
Office 365 offers robust functionality to enhance external communication for businesses. It facilitates seamless collaboration, document sharing, and real-time communication with external partners and clients.
The platform ensures a secure environment for businesses when sharing documents with external parties. Leveraging OneDrive, a cloud-based storage system, enables businesses to safely store and exchange documents with external partners and clients, eliminating concerns about data security.
Office 365 offers businesses the capability to engage in instant communication with external partners and clients. Through Skype for Business, enterprises can effortlessly arrange video conferences and exchange messages with external partners and clients, transcending time zone constraints and cutting down on travel expenses.
Additionally, Office 365 equips businesses with the capacity to cooperate with external partners and clients. Using SharePoint, businesses can swiftly generate and distribute documents to collaborate on projects with external partners and clients, eliminating concerns about the security of data.
In essence, Office 365 serves as a robust instrument for enhancing communication with external partners and clients. By leveraging Office 365, businesses seamlessly exchange documents, engage in real-time communication, and collaborate on projects with external partners and clients, all while safeguarding data integrity and overcoming time zone barriers.
Leveraging Office 365 to Enhance Collaboration with External Partners and Clients
Office 365, a robust suite of cloud-based applications, offers organizations an opportunity to fortify collaboration with external partners and clients. By leveraging Office 365, organizations effortlessly exchange documents, engage in real-time communication, and retrieve data from any location.
The secure platform of Office 365 fosters seamless collaboration with external partners and clients. This eliminates concerns about document security, as users can easily share encrypted documents, spreadsheets, and presentations with external parties. These files are securely stored in the cloud, maintaining their integrity.
Moreover, Office 365 serves as a conduit for real-time communication. Utilizing Skype for Business, organizations can engage in live discussions with external partners and clients through voice and video calls, as well as instant messaging. This facilitates continuous engagement and prompt issue resolution.
Furthermore, Office 365 provides unrestricted access to data. Organizations can effortlessly retrieve their data from any device, at any given time. This empowers them to stay abreast of developments with their external partners and clients, swiftly attending to any changes or requests.
Overall, Office 365 is a powerful suite of cloud-based applications that can help organizations enhance collaboration with external partners and clients. It provides a secure platform for sharing documents, a platform for real-time communication, and access to data from anywhere. With Office 365, organizations can easily collaborate with external partners and clients, and ensure that their data remains secure.
How Office 365 Can Help Streamline Communication with External Partners and Clients
The Office 365 suite offers a robust array of tools designed to optimize and expedite communication with external partners and clients. This encompassing platform enables seamless real-time collaboration regardless of geographical barriers.
One notable component of Office 365 is Microsoft Teams, a robust collaboration platform facilitating instant messaging, file sharing, and concurrent project collaboration. Furthermore, it facilitates the arrangement of virtual meetings, thereby fostering sustained connectivity with external partners and clients.
In addition to collaborative tools, Office 365 encompasses an array of email and calendar functionalities. Outlook, for instance, empowers users to effortlessly manage emails, schedule meetings, and maintain contact databases while ensuring cross-device accessibility for streamlined connectivity on the move.
Moreover, Office 365 is fortified with an array of security features poised to safeguard sensitive data during interactions with external partners and clients. Notably, it integrates encryption for emails and files along with two-factor authentication to fortify security.
Ultimately, Office 365 emerges as a robust and multifaceted tool suite aimed at optimizing and securing communication with external partners and clients, bolstering connectivity and fortifying security protocols.
Conclusion
Office 365 is an excellent tool for businesses to use to communicate and collaborate with external partners and clients. It provides a secure platform for sharing documents, files, and other information, as well as a variety of tools for communication and collaboration. It is easy to use and can be accessed from any device, making it a great choice for businesses that need to stay connected with their external partners and clients. With Office 365, businesses can ensure that their communication and collaboration efforts are secure, efficient, and effective.
Troubleshooting common Office 365 issues
“Solve Office 365 Problems Quickly and Easily – Troubleshoot with Confidence!”
Introduction
Office 365, a robust set of cloud-based tools, enhances productivity and fosters collaboration in businesses of varying scales. Yet, as with any technology, Office 365 encounters glitches that impede workflow and prompt irritation. Thankfully, there exist several troubleshooting measures to address prevalent Office 365 hitches. This guidance will outline key issues and offer strategies to resolve them.
How to Troubleshoot Common Office 365 Security Issues
Office 365 is a powerful suite of cloud-based applications that can help businesses of all sizes increase productivity and collaboration. However, with the increased use of cloud-based applications comes the need for increased security. In this article, we will discuss some of the most common Office 365 security issues and how to troubleshoot them.
1. Unlawful Entry: Unauthorized access poses a prevalent security threat to Office 365. Mitigating this risk entails enforcing robust, regularly updated passwords for all users, and mandating two-factor authentication.
2. Deceptive Ploys: Office 365 is susceptible to phishing attacks. Safeguarding against such threats requires educating users on identifying and evading deceptive emails. Additionally, Office 365 has built-in anti-phishing protection that can help detect and block malicious emails.
3. Data loss poses a significant security risk within Office 365. Regular data backups are crucial to mitigate this risk. Equally essential is training users on proper data handling and sharing protocols.
4. The omnipresent threat of malware infection in Office 365 demands attention. Equipping all users with updated antivirus software for their devices is a critical defense measure. Furthermore, Office 365’s integrated malware protection serves as an additional barrier against harmful files.
Abiding by these measures fortifies the security of Office 365 environments for businesses. It is imperative for businesses to continually assess and refine their security policies and procedures to assure their relevance and efficacy.
How to Troubleshoot Common Office 365 Performance Issues
Office 365 is a powerful suite of cloud-based applications that can help businesses of all sizes increase productivity and collaboration. However, like any technology, Office 365 can experience performance issues. To ensure that your Office 365 applications are running smoothly, it is important to troubleshoot any performance issues as soon as they arise. Here are some tips for troubleshooting common Office 365 performance issues.
1. Before delving into the complexities of troubleshooting Office 365 performance, it is imperative to first assess the integrity of your network connection. Ensuring that your network is operating at its peak capacity and devoid of any connectivity hitches is paramount. In cases where a wireless connection is utilized, ascertaining its robustness and absence of interference becomes equally crucial.
2. The performance hiccups encountered with Office 365 might stem from your computer’s inadequate resources. Verifying that ample RAM and storage space are available to seamlessly run Office 365 applications is crucial. In instances where resource scarcity is evident, contemplating hardware upgrades or augmenting RAM and storage becomes a requisite consideration.
3. The settings within Office 365 wield considerable influence on its performance. It is imperative to meticulously configure these settings tailored to your specific environment. For instance, in a shared workspace, ensuring the employment of suitable settings for document and application sharing is indispensable.
4. The vitality of running the latest iterations of Office 365 cannot be overstated. Regularly checking for updates to ensure that your Office 365 suite and all associated applications are current is imperative.
5. The detrimental impacts of malware on performance, including within Office 365, are well-documented. Conducting thorough system scans to rid your computer of any malware and safeguard its integrity is pivotal.
6. Should the aforementioned measures fail to assuage the Office 365 performance woes, enlisting the aid of Microsoft Support emerges as the next step. Their expertise can prove instrumental in pinpointing and redressing any underlying issues precipitating the performance concerns.
By following these steps, you can troubleshoot common Office 365 performance issues and ensure that your applications are running smoothly.
How to Troubleshoot Common Office 365 Installation Issues
The process of installing Office 365 may initially seem straightforward, yet unforeseen complications may occasionally surface. If you encounter obstacles during the installation of Office 365, the following troubleshooting tips may aid in resolving the issue.
1. System Requirements Verification: Prior to commencing the installation of Office 365, undertaking an assessment of whether your computer aligns with the minimum system requirements for the software is imperative. Office 365 necessitates a PC operating on Windows 7 or later, or a Mac operating on OS X 10.10 or later.
2. Assessment of Internet Connectivity: A dependable internet connection stands as a prerequisite for the seamless installation of Office 365. If impediments arise during the installation process, assuring the adequacy of your internet connection is indispensable.
3. Evaluation of Antivirus Software: Certain antivirus programs possess the capacity to impede the integration of Office 365. Should complications emerge during the installation, confirming that your antivirus software does not obstruct the process is crucial.
4. Scrutiny of Firewall Settings: Firewalls, too, harbor the potential to disrupt the installation of Office 365. Ensuring that your firewall settings do not hinder the installation process is integral.
5. Validation of Office 365 Subscription: Ensuring the active and up-to-date status of your Office 365 subscription stands as a pivotal step. The absence of an active subscription renders the installation of Office 365 unattainable.
6. Pursuit of Updates: Verifying that your computer is equipped with the latest Windows or Mac updates is paramount. Obsolete operating systems have the potential to manifest issues during the installation of Office 365.
7. Elimination of Previous Office Versions: If impediments materialize during the installation of Office 365, eradication of any prior versions of Office remains a vital step.
8. Engagement with Microsoft Support: In the event that challenges persist during the installation process, seeking assistance from Microsoft Support serves as a prudent course of action.
Adhering to these troubleshooting guidelines is anticipated to culminate in the resolution of any installation dilemmas encountered within the realm of Office 365.
How to Troubleshoot Common Office 365 Email Issues
Office 365 is a powerful and reliable email platform, but like any technology, it can experience issues. Fortunately, there are a few steps you can take to troubleshoot common Office 365 email issues.
1. Check Your Internet Connection: The first step in troubleshooting any Office 365 email issue is to check your internet connection. Make sure your connection is stable and that you have a strong signal. If you are using a wireless connection, try switching to a wired connection.
2. Check Your Email Settings: If your internet connection is stable, the next step is to check your email settings. Make sure your settings are correct and that you are using the correct ports and encryption protocols.
3. Check Your Email Filters: If your settings are correct, the next step is to check your email filters. Make sure your filters are not blocking any emails or preventing them from being delivered.
4. Check Your Email Quota: If your filters are not the issue, the next step is to check your email quota. Make sure you have enough storage space for your emails. If you are running low on storage space, you may need to delete some emails or upgrade your storage plan.
5. Check Your Email Client: If your email quota is not the issue, the next step is to check your email client. Make sure your email client is up to date and that it is compatible with Office 365.
6. Contact Support: If you have tried all of the above steps and are still experiencing issues, the next step is to contact Office 365 support. They can help you troubleshoot the issue and provide additional assistance if needed.
By following these steps, you should be able to troubleshoot most common Office 365 email issues. If you are still having issues, contact Office 365 support for additional assistance.
How to Troubleshoot Common Office 365 Login Issues
Office 365, a formidable array of tools tailored to enhance productivity and collaboration across businesses, regardless of their scale, can encounter occasional operational hiccups that impede user access.
1. Verify Your Credentials: The ubiquitous source of Office 365 login impediments often stems from erroneous credentials. Ensure precise input of your username and password. In case of uncertainty, opt to reset your password or seek guidance from your IT administrator.
2. Validate Your Network Connectivity: When grappling with login issues, an essential step involves confirming the seamless operation of your network connection. Explore alternative network options or reboot your router to troubleshoot.
3. Check Your Browser: Office 365 requires a modern web browser to work properly. Make sure you are using the latest version of your preferred browser.
4. Check Your Firewall Settings: If you are having trouble logging in, make sure your firewall is not blocking Office 365. You may need to add an exception for Office 365 in your firewall settings.
5. Check Your Antivirus Software: Some antivirus software can interfere with Office 365. Make sure your antivirus software is up to date and that it is not blocking Office 365.
6. Check Your Office 365 Subscription: If you are having trouble logging in, make sure your Office 365 subscription is active. If your subscription has expired, you will need to renew it in order to access Office 365.
By following these tips, you should be able to troubleshoot most common Office 365 login issues. If you are still having trouble logging in, contact your IT administrator for assistance.
Conclusion
Troubleshooting common Office 365 issues can be a daunting task, but with the right tools and knowledge, it can be done quickly and efficiently. By understanding the different components of Office 365, understanding the different types of issues that can arise, and having the right tools and resources to help you troubleshoot, you can quickly and effectively resolve any Office 365 issue. With the right knowledge and resources, you can ensure that your Office 365 environment is running smoothly and efficiently.
Using Office 365 for data loss prevention (DLP)
“Secure Your Data with Office 365 DLP – Protect Your Business from Data Loss!”
Introduction
Office 365, a robust cloud-based platform, offers a diverse array of tools and services to aid businesses in data management. An essential facet of Office 365 is its adept data loss prevention (DLP) capabilities. DLP encompasses a suite of tools and procedures designed to safeguard organizations’ sensitive data from illicit access, inadvertent loss, or malevolent breaches. Utilizing Office 365, businesses can seamlessly establish DLP policies to oversee and fortify their data, in addition to crafting alerts and notifications for unauthorized data access or inappropriate sharing. This article delves into the utilization of Office 365 for data loss prevention and its ensuing benefits.
How to Monitor and Manage Data Loss Prevention in Office 365
Data Loss Prevention (DLP) plays a crucial role in safeguarding sensitive information within Office 365 for organizations. It acts as a barrier against unauthorized access, usage, or disclosure of such data, thereby ensuring a secure environment for sensitive information flow management.
To initiate DLP within Office 365, organizations must initially outline the categories of data necessitating protection, encompassing confidential, sensitive, and regulated data. Subsequently, these identified data types form the basis for creating DLP policies, which serve to oversee and safeguard such data.
The establishment of DLP policies occurs within the Office 365 Security & Compliance Center. Here, organizations stipulate the data types to protect, the storage locations of such data, and the corresponding actions upon policy triggers. This can involve blocking data sharing or issuing alerts to users or administrators.
Moreover, DLP extends to overseeing and controlling data movement within the Office 365 ecosystem, encompassing activities like email and file sharing within the organization. Rules are configured to detect and act upon the sharing of sensitive data to prevent unauthorized dissemination.
Regular review of DLP policies is imperative to maintain their relevance and effectiveness. Simultaneously, scrutinizing DLP reports aids in identifying potential data breaches and security concerns.
Through vigilant surveillance and management of data loss prevention in Office 365, organizations fortify their defenses, ensuring that sensitive data remains shielded from unauthorized access and compliance with data privacy regulations is upheld.
Best Practices for Implementing Office 365 DLP in Your Organization
Implementing Data Loss Prevention (DLP) is a vital strategic measure for any organization leveraging Office 365. DLP serves to safeguard confidential information from unauthorized access and mitigate inadvertent or deliberate misuse, as well as malicious assaults. This implementation is crucial to ensuring that organizational data remains secure and adheres to industry standards. Here are key guidelines for instituting Office 365 DLP effectively within your organization:
1. Identify Sensitive Data: The initial phase involves pinpointing the categories of data that necessitate protection, such as classified, delicate, or data subject to industry regulations. This proactive identification of crucial data forms the basis for formulating and enforcing policies and regulations that fortify its security.
2. Create Policies and Rules: Subsequent to recognizing the data necessitating protection, the formulation of distinct policies and regulations sets the framework for its preservation. These guidelines must be custom-tailored to the organization’s precise requirements and subject to regular scrutiny and updating.
3. Monitor and Audit: Upon crafting policies and regulations, monitoring and conducting periodic audits are essential. This ongoing assessment verifies adherence to the established norms and unearths potential security vulnerabilities that require prompt attention.
4. Educate Employees: Employee literacy on the significance of data security and familiarity with the established policies and regulations are of paramount importance. This initiative reinforces employee understanding of the criticality of data security while promoting their awareness of the prevailing policies and regulations.
5. Utilize Automation: Leveraging automation can enhance the efficiency of DLP implementation. Automation assists in the identification of sensitive data, establishment of policies and regulations, monitoring, auditing, and employee education.
By following these best practices, organizations can fortify their security posture and ensure compliance with industry regulations. The implementation of DLP acts as a bulwark against unauthorized access, inadvertent or deliberate misuse, and malicious intrusions to shield sensitive organizational data.
Understanding the Different Types of Data Loss Prevention in Office 365
Data loss prevention, commonly referred to as DLP, stands as a pivotal safeguard for any organization. Office 365 delivers a myriad of DLP features aimed at fortifying data protection. Acquainting oneself with the diverse DLP options within Office 365 empowers one to safeguard and uphold the integrity of their data in alignment with industry standards and regulations.
Content inspection emerges as the initial category of DLP in Office 365.This feature allows you to scan emails, documents, and other content for sensitive information, such as credit card numbers or Social Security numbers. You can also set up rules to block or quarantine content that contains sensitive information.
In Office 365, the second variant of DLP pertains to data encryption, allowing the encryption of data within the platform, encompassing emails, documents, and other content, ensuring restricted access solely to authorized users, safeguarding against unauthorized entry.
The third category of DLP involves the implementation of data loss prevention policies, enabling the establishment of regulations to avert inadvertent or deliberate dissemination of sensitive data. For instance, a policy may proscribe the transmission of emails containing confidential information to external addressees.
Furthermore, Office 365 offers an array of reporting and auditing functionalities to facilitate monitoring and tracing of data loss prevention endeavors. These tools enable the scrutiny of DLP events, including obstructed emails or sequestered documents, and the generation of comprehensive reports to pinpoint potential data loss vulnerabilities.
Acquiring knowledge about the diverse DLP options within Office 365 is instrumental in ensuring the security and adherence of your data to industry standards. Implementing apt DLP protocols can substantially fortify your organization against data breaches and guarantee the perpetuity of data security.
Exploring the Benefits of Office 365 DLP for Data Security
Safeguarding data has become a paramount concern for businesses across the spectrum. The surge in cybercrime dictates that organizations take proactive measures to shield their sensitive data from malevolent entities. Office 365 Data Loss Prevention (DLP) emerges as a potent instrument for organizations to fortify their data security and uphold conformity with industry mandates.
Office 365 DLP, a cloud-based service, furnishes organizations with a robust arsenal to shield their sensitive data. It encompasses an extensive array of features for data detection, surveillance, and fortification. Through Office 365 DLP, organizations can pinpoint and categorize sensitive data, establish protocols to govern data usage, and oversee data utilization to guarantee adherence to industry directives.
The merits of Office 365 DLP for organizations are manifold. Primarily, it serves as a bulwark against unauthorized access to sensitive data. By identifying and classifying such data, organizations can ensure that only authorized personnel can avail of it. Furthermore, Office 365 DLP aids organizations in conforming to industry regulations. By instituting protocols to regulate the handling of data, organizations can ensure adherence to pertinent regulations. Finally, Office 365 DLP can help organizations monitor data usage. By monitoring data usage, organizations can ensure that their data is being used appropriately and that any unauthorized access is detected and addressed.
Overall, Office 365 DLP is a powerful tool that can help organizations protect their data and ensure compliance with industry regulations. By identifying and classifying sensitive data, setting policies to control how data is used, and monitoring data usage, organizations can ensure that their data is secure and that they are in compliance with applicable regulations.
How Office 365 DLP Can Help Protect Your Business from Data Loss
Data loss prevention (DLP) is an important security measure for any business. It helps protect sensitive data from unauthorized access, accidental or intentional misuse, and malicious attacks. With the rise of cloud computing, businesses are increasingly turning to Office 365 for their data storage and collaboration needs. Office 365 provides a comprehensive set of DLP features to help protect your business from data loss.
Office 365 DLP helps protect your business by monitoring and controlling the flow of sensitive data. It can detect and block the transmission of sensitive data, such as credit card numbers, Social Security numbers, and other confidential information. It can also detect and block the sharing of sensitive documents, such as contracts and financial statements.
Office 365 DLP also helps protect your business by providing visibility into how sensitive data is being used. It can detect when sensitive data is being shared with unauthorized users, and alert you to potential data breaches. It can also detect when sensitive data is being stored in an insecure location, such as a public cloud storage service.
Office 365 DLP also helps protect your business by providing customizable policies to control how sensitive data is used. You can set up policies to restrict the sharing of sensitive data, or to require additional authentication before sensitive data can be accessed. You can also set up policies to require encryption for sensitive data, or to block the downloading of sensitive data.
Office 365 DLP is an important security measure for any business. It helps protect sensitive data from unauthorized access, accidental or intentional misuse, and malicious attacks. With Office 365 DLP, you can monitor and control the flow of sensitive data, detect potential data breaches, and set up policies to control how sensitive data is used. By taking advantage of Office 365 DLP, you can help protect your business from data loss.
Conclusion
Office 365’s data loss prevention (DLP) capabilities are a powerful tool for organizations looking to protect their sensitive data. With its comprehensive set of features, Office 365 DLP can help organizations identify, monitor, and protect their data from unauthorized access and accidental or malicious data loss. It also provides organizations with the ability to customize their DLP policies to meet their specific needs. With Office 365 DLP, organizations can ensure that their data is secure and protected from unauthorized access and data loss.
Implementing data governance and retention policies in Office 365
“Secure Your Data with Office 365: Implementing Data Governance and Retention Policies for Maximum Protection.”
Introduction
The implementation of data governance and retention policies holds pivotal importance within organizations, ensuring the security and compliance of their data in accordance with industry regulations. Integration of these policies within Office 365 serves as a safeguard for organizations, guaranteeing the secure and compliant management of their data. Office 365 offers an array of tools and features tailored for establishing data governance and retention policies, encompassing data loss prevention, eDiscovery, and retention labels. This piece aims to elucidate the significance of integrating data governance and retention policies in Office 365, while presenting a comprehensive overview of the available tools and features to facilitate this process.
How to Automate Data Governance and Retention Policies in Office 365
Implementing robust data governance and retention policies is imperative for organizations to uphold data security and compliance with industry mandates. Within Office 365, the automation of such policies is pivotal for efficient and secure data management.
The initial phase of automating data governance and retention policies in Office 365 involves formulating a comprehensive data governance plan. This plan must delineate the different data categories requiring management, stipulate their respective retention periods, and prescribe requisite security protocols for data safeguarding. Upon its establishment, the plan serves as the framework for the creation of essential policies within Office 365.
Subsequently, configuring these policies in Office 365 is essential, and this can be achieved through the Office 365 Security & Compliance Center. Here, administrators wield the ability to instate policies facilitating automated data deletion after specific timeframes, or to enforce access constraints on particular data categories. Additionally, the setup of alerts to signal data access or modification instances is also possible.
Conclusively, vigilant monitoring of the data governance and retention policies is indispensable. Regular scrutiny via the Office 365 Security & Compliance Center permits administrators to scrutinize reports detailing the policies’ adherence and intervene if necessary.
By standardizing the automation of data governance and retention policies in Office 365, organizations can fortify the safeguarding of their data and adhere to industry regulations, ultimately fortifying their reputation as a trustworthy and secure entity.
How to Leverage Office 365 Security and Compliance Tools for Data Governance
Data governance plays a crucial role in an organization’s overall security and compliance framework. As the management of data becomes increasingly intricate, it is imperative for organizations to guarantee the security and compliance of their data in line with industry regulations. Office 365 offers an array of robust security and compliance tools that can be harnessed to uphold effective data governance.
The initial phase in harnessing the power of Office 365’s security and compliance tools for data governance involves gaining a comprehensive understanding of the data under management. Organizations need to categorize the types of data they store and assess the associated risks. This assessment is pivotal in determining the requisite security and compliance protocols that must be put in place.
Once the data is identified, organizations should utilize Office 365’s security and compliance tools to fortify it. The platform offers a diverse set of tools, encompassing encryption, data loss prevention, and multi-factor authentication, that serve to fortify and ensure the compliance of the data with industry standards.
Furthermore, leveraging Office 365’s compliance tools is paramount for data monitoring and auditing. The suite provides a variety of tools for monitoring data utilization and detecting any irregularities. This proactive approach can safeguard data usage in alignment with organizational policies and industry regulations.
Ultimately, to effectively track data usage and ensure compliance, organizations can utilize Office 365’s reporting tools. These tools enable organizations to monitor data usage and identify potential concerns, thus supporting adherence to organizational policies and industry regulations.
By harnessing the capabilities of Office 365’s security and compliance tools, organizations can establish robust safeguards to ensure the security and compliance of their data in accordance with industry regulations. This proactive strategy not only assures adherence to policies and regulations but also serves to shield the organization against potential data breaches.
How to Monitor and Enforce Data Governance Policies in Office 365
Ensuring security and compliance in any organization hinges on robust data governance. Within Office 365, data governance policies play a pivotal role in safeguarding and regulating data usage. Implementing these policies necessitates vigilant monitoring and enforcement within the Office 365 environment.
The initial phase of upholding data governance policies involves crafting a comprehensive data governance plan. This plan should include the policies and procedures that will be used to manage and protect data in Office 365. It should also include the roles and responsibilities of each user and the processes for monitoring and enforcing the policies.
Once the data governance plan is established, organizations ought to actively leverage the inherent security and compliance functionalities within Office 365 to rigorously oversee and uphold the established policies. These functionalities encompass data loss prevention (DLP) policies, which are instrumental in identifying and thwarting unauthorized dissemination of sensitive data. Furthermore, organizations can harness Office 365’s robust auditing and reporting capabilities to vigilantly surveil user activity and pinpoint potential breaches of policies.
Moreover, organizations should capitalize on Office 365’s access control mechanisms to meticulously regulate access to sensitive data, ensuring that solely authorized individuals are granted entry. This can be achieved by configuring user roles and allotting precise permissions to each role. Additionally, employing Office 365’s multi-factor authentication will fortify the assurance that only authorized users can gain access to critical data.
Ultimately, organizations should implement Office 365’s meticulous data retention policies to guarantee the appropriate preservation of data for requisite durations. This serves to circumvent unwarranted data retention and ensures the secure disposal of data when it becomes obsolete.
By diligently following these measures, organizations can effectively ensure the stringent surveillance and enforcement of their data governance policies within the Office 365 environment. Consequently, this will culminate in the meticulous and secure management of data, aligning with regulatory compliance standards.
Best Practices for Implementing Data Retention Policies in Office 365
Effective data retention strategies are integral to comprehensive data management frameworks within any organization. In the realm of Office 365, these strategies play a pivotal role in facilitating meticulous control over data and ensconcing it securely in adherence to pertinent legislations and regulations.
Amid the implementation of data retention strategies in Office 365, several salient best practices warrant consideration.
Firstly, a paramount practice involves the formulation of lucid policies delineating the categories of data to be retained, the duration of retention, as well as the prerequisites for data eradication. These policies should be meticulously documented and disseminated across all users within the organization.
Secondly, leveraging retention labels emerges as a potent mechanism for orchestrating data retention within Office 365, affording organizations the ability to imbue specific types of data, encompassing emails, documents, and other diverse content, with tailored retention policies.
Additionally, vigilantly monitoring compliance with these data retention policies is imperative, ensuring the steadfast adherence to requisite data retention and deletion requisites.
Finally, a proactive approach entails educating users on the intricacies of data retention policies and instilling an understanding of the pivotal role of adherence to these policies.
Use Automation: Automation can help organizations ensure that their data retention policies are enforced consistently. Automated processes can be used to apply retention labels, monitor compliance, and delete data when it is no longer needed.
By following these best practices, organizations can ensure that their data retention policies are implemented effectively in Office 365. This will help them maintain control over their data and ensure that it is stored securely and in compliance with applicable laws and regulations.
How to Establish a Data Governance Framework in Office 365
A robust information management strategy necessitates the integration of data governance into an organization’s operational framework. This underpins the secure, compliant, and efficient management of data. In the context of Office 365, data governance is operationalized through the utilization of a comprehensive framework, comprising policies, processes, and tools, designed to facilitate the secure and compliant management of organizational data.
Initiating the establishment of a data governance framework within Office 365 involves delineating its scope, encompassing the identification of relevant data sets and the delineation of roles and responsibilities for data management, while concomitantly defining the overarching objectives, including data security, compliance, and operational efficiency.
Following the definitive demarcation of the framework’s scope, the subsequent phase entails formulating a meticulous data governance plan, incorporating the delineation of policies, processes, and tools for data management, alongside crafting a timeline for implementation and a budget to accommodate associated expenses.
Upon the formulation of the plan, the focus shifts to the implementation of the data governance framework, encompassing the establishment of requisite tools and processes, such as data classification, retention, and access policies, balanced with the imperative of regular monitoring and updates to uphold its effectiveness.
Crucially, effective communication of the data governance framework to all stakeholders is paramount, compelling the provision of comprehensive training for data custodians, coupled with the dissemination of awareness among all users regarding data governance protocols and procedures.
By executing these meticulous steps, organizations can establish a robust data governance framework within Office 365, engendering the secure, compliant, and efficient management of their data assets.
Conclusion
In conclusion, implementing data governance and retention policies in Office 365 is a great way to ensure that your organization’s data is secure and compliant with industry regulations. It also helps to ensure that data is properly managed and stored, and that it is available when needed. By taking the time to properly implement data governance and retention policies in Office 365, organizations can ensure that their data is secure and compliant, and that it is available when needed.
