Posts Tagged ‘503 service unavailable’
SharePoint Server 2007, 2010, 2013 HTTP Error 503. The service is unavailable
From last few days I have seen lot of people come across error 503 Service Unavailable. Mostly people come up with Plan to update password to resolve the issue. It is 90 % of time that Update Password in IIS and Central Admin does the trick but if you come across a scenario where you are still stuck with “503 Service Unavailable” try below. Verify that all SharePoint services are started, this error mostly occurs because of changing the service account password.
Here is screenshot of error how it looks
Error you might see in Log file
Exception: System.ServiceModel.ServiceActivationException: The service ‘/SecurityTokenServiceApplication/securitytoken.svc’ cannot be activated due to an exception during compilation. The exception message is: Exception has been thrown by the target of an invocation.. —> System.Reflection.TargetInvocationException: Exception has been thrown by the target of an invocation. —>
What is “503 Service Unavailable” error?
Http 503 errors are generated by the IIS and it happens when web server sends data stream back to the web site.
+> First I would like to make sure below steps are followed to update the password.
- Open IIS on SharePoint server > Expand Server > Expand Website
- Check the web site properties in IIS > under home directory tab, check the application pool value and then open that application pool from the application pools (separate node in the IIS tree)
- Click the identity tab and see who the pool is assigned to. For the sake of testing, you can select “Predefined” and select local service from the drop down.
- Restart IIS and see if things work out for you.
- You may need to change the new password to SharePoint timer service in services.msc console.
Here are the Advance troubleshooting steps I followed to resolve this issue
- Incorrect Authentication Settings: Please ensure that the authentication settings for the SecureTokenServiceApplication are correctly configured by completing the following steps:a) Open IIS Manager
Expand “Sites”
Expand “SharePoint Web Services”
Select “SecurityTokenServiceApplication”
From the “Features” pane, double click on “Authentication” under “IIS”
Right click “Forms Authentication” and select “Disable”
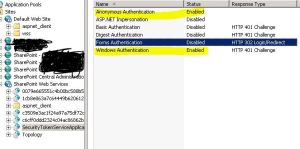 The authentication settings page should only have Windows and Anonymous access enable for the security token service to issue tokens properly (and for claims authentication to work properly)
The authentication settings page should only have Windows and Anonymous access enable for the security token service to issue tokens properly (and for claims authentication to work properly)
- Incorrect data in the configuration file: Please review the web.config file of the secure token service application and compare it to a web.config file from a “working” secure token service application or secure token service application on different machine. Lot of people event copy web.config from a working machine which resolves the issue. Here is a copy of my web.config for security token
———————- Security Token Service Application web.config———–Start ——————
<?xml version=”1.0″ encoding=”utf-8″ ?>
<configuration>
<system.serviceModel>
<!– Behavior List: –>
<behaviors>
<serviceBehaviors>
<behavior name=”SecurityTokenServiceBehavior” >
<!– The serviceMetadata behavior allows one to enable metadata (endpoints, bindings, services) publishing.
This configuration enables publishing of such data over HTTP GET.
This does not include metadata about the STS itself such as Claim Types, Keys and other elements to establish a trust.
–>
<serviceMetadata httpGetEnabled=”true” />
<!– Default WCF throttling limits are too low –>
<serviceThrottling maxConcurrentCalls=”65536″ maxConcurrentSessions=”65536″ maxConcurrentInstances=”65536″ />
</behavior>
<behavior name=”ApplicationSecurityTokenServiceBehavior” >
<serviceMetadata httpGetEnabled=”false” httpsGetEnabled=”false” />
<serviceThrottling maxConcurrentCalls=”65536″ maxConcurrentSessions=”65536″ maxConcurrentInstances=”65536″ />
</behavior>
</serviceBehaviors>
</behaviors>
<!– Service List: –>
<services>
<service name=”Microsoft.IdentityModel.Protocols.WSTrust.WSTrustServiceContract”
behaviorConfiguration=”SecurityTokenServiceBehavior” >
<!– This is the HTTP endpoint that supports clients requesing tokens. This endpoint uses the default standard ws2007HttpBinding which requires that clients authenticate using their Windows credentials. –>
<endpoint
address=””
binding=”customBinding”
bindingConfiguration=”spStsBinding”
contract=”Microsoft.IdentityModel.Protocols.WSTrust.IWSTrust13SyncContract” />
<!– This is the HTTP endpoint that supports clients requesting service tokens. –>
<endpoint
name =”ActAs”
address=”actas”
binding=”customBinding”
bindingConfiguration=”spStsActAsBinding”
contract=”Microsoft.IdentityModel.Protocols.WSTrust.IWSTrust13SyncContract” />
<!– This is the HTTP endpoint that supports IMetadataExchange. –>
<endpoint address=”mex”
binding=”mexHttpBinding”
contract=”IMetadataExchange” />
</service>
<service
name=”Microsoft.SharePoint.IdentityModel.ApplicationSecurityTokenService”
behaviorConfiguration=”ApplicationSecurityTokenServiceBehavior”>
<endpoint
name=”app”
address=””
binding=”customBinding”
bindingConfiguration=”spStsApplicationBinding” contract=”Microsoft.SharePoint.IdentityServices.IApplicationSecurityTokenServiceContract” />
</service>
<servicename=”Microsoft.SharePoint.Administration.Claims.SPWindowsTokenCacheService”>
<endpoint address=””
binding=”customBinding”
bindingConfiguration=”SPWindowsTokenCacheServiceHttpsBinding” contract=”Microsoft.SharePoint.Administration.Claims.ISPWindowsTokenCacheServiceContract” />
</service>
</services>
<!– Binding List: –>
<bindings>
<customBinding>
<binding
name=”spStsBinding”>
<binaryMessageEncoding>
<readerQuotas
maxStringContentLength=”1048576″
maxArrayLength=”2097152″/>
</binaryMessageEncoding>
<httpTransport
maxReceivedMessageSize=”2162688″
authenticationScheme=”Negotiate”
useDefaultWebProxy=”false” />
</binding>
<binding
name=”spStsActAsBinding”>
<security
authenticationMode=”SspiNegotiatedOverTransport”
allowInsecureTransport=”true”
defaultAlgorithmSuite=”Basic256Sha256″ messageSecurityVersion=”WSSecurity11WSTrust13WSSecureConversation13WSSecurityPolicy12″ />
<binaryMessageEncoding>
<readerQuotas
maxStringContentLength=”1048576″
maxArrayLength=”2097152″/>
</binaryMessageEncoding>
<httpTransport
maxReceivedMessageSize=”2162688″
authenticationScheme=”Negotiate”
useDefaultWebProxy=”false”/>
</binding>
<binding
name=”spStsApplicationBinding”>
<binaryMessageEncoding>
<readerQuotas
maxStringContentLength=”1048576″
maxArrayLength=”2097152″ />
</binaryMessageEncoding>
<namedPipeTransport
maxPendingAccepts=”250″
maxPendingConnections=”250″
maxReceivedMessageSize=”2162688″>
<connectionPoolSettings
idleTimeout=”00:30:00″
maxOutboundConnectionsPerEndpoint=”250″/>
</namedPipeTransport>
</binding>
<binding name=”SPWindowsTokenCacheServiceHttpsBinding”>
<security
authenticationMode=”IssuedTokenOverTransport”
defaultAlgorithmSuite=”Basic256Sha256″ />
<textMessageEncoding>
<readerQuotas maxStringContentLength=”1048576″ maxArrayLength=”2097152″/>
</textMessageEncoding>
<httpsTransport maxReceivedMessageSize=”2162688″ authenticationScheme=”Anonymous” useDefaultWebProxy=”false” />
</binding>
</customBinding>
</bindings>
</system.serviceModel>
<system.webServer>
<security>
<authentication>
<anonymousAuthentication enabled=”true” />
<windowsAuthentication enabled=”true”>
<providers>
<clear />
<add value=”Negotiate” />
<add value=”NTLM” />
</providers>
</windowsAuthentication>
</authentication>
</security>
<modules>
<add name=”WindowsAuthenticationModule” />
</modules>
</system.webServer>
<system.net>
<connectionManagement>
<clear />
<add address=”*” maxconnection=”10000″ />
</connectionManagement>
</system.net>
</configuration>
———————- Security Token Service Application web.config———–End ——————
- SecureTokenServiceApplication not provisioned: Use the following power shell commands to provision the secure token service application
$sts = Get-SPServiceApplication | ?{$_ -match “Security”}
$sts.Status
$sts.Provision()
$farm = [Microsoft.SharePoint.Administration.SPFarm]::Local
$webServiceCollection = new-object Microsoft.SharePoint.Administration.SPWebServiceCollection($farm)
foreach ($service in $webServiceCollection)
After I run above command I got below error:
Exception calling “SecurityTokenForContext” with “1” argument(s): “The requested service,’http://localhost:32843/SecurityTokenServiceApplication/securitytoken.svc/actas’ could not be activated. See the server’s diagnostic trace logs
- > If you get above error try below in powershell
$sts = Get-SPServiceApplication | ?{$_ -match “Security”}
$sts.Status
$sts.Provision()
Event log :
The Execute method of job definition Microsoft.SharePoint.Publishing.Internal.PersistedNavigationTermSetSyncJobDefinition.
ULS log :
The HTTP service located at http://localhost:32843/SecurityTokenServiceApplication/securitytoken.svc/actas is unavailable. This could be because the service is too busy or because no endpoint was found listening at the specified address. Please ensure that the address is correct and try accessing the service again later
+> If you get above in Powershell try below:
PSCONFIG.EXE -cmd upgrade -inplace b2b –force
Psconfig -cmd Secureresources
Note: Above needs to run in SharePoint Powershell with account which has Farm Admin permission.
- You might have the URL http://+:80 reserved. To check the same run command “netsh http show urlacl” in SharePoint Powershell. If this shows an output similar to
Reserved URL : http://+:80/
User: BUILTIN\IIS_IUSRS
Listen: Yes
Delegate: Yes
User: BUILTIN\Administrators
Listen: Yes
Delegate: Yes
User: NT AUTHORITY\NETWORK SERVICE
Listen: Yes
Delegate: Yes
SDDL: D:(A;;GA;;;IS)(A;;GA;;;BA)(A;;GA;;;NS)
Then you have this port reserved which takes precedence over your http://localhost calls. Go ahead and remove this URL reservation by running the following command,
netsh http delete urlacl url=http://+:80/
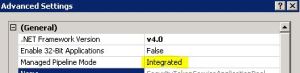
- Web Application started out as a 32-bit ASP.NET application, and subsequently got converted (upgraded) to a SharePoint 2010 Web Application. In this case you will see that the application pool has the “Enable 32-Bit Applications” property set to true, which is incompatible with SharePoint 2010. Setting this property to false should solve the problem. In some cases some SharePoint 2013 server Web Applications have this setting as true which is incorrect
Ensure that the enable32BitAppOnWin64 setting for the “SharePoint Central Administration” app pool is set to False, and the same for Other Application pool
+> You can do the same by Editing applicationHost.config located at C:\Windows\System32\inetsrv\config :
Change:
<globalModules>
…
<add name=”SharePoint14Module” image=”C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\14\isapi\owssvr.dll” preCondition=”appPoolName=SharePoint Central Administration v4″ />
</globalModules>
To:
<add name=”SharePoint14Module” image=”C:\Program Files\Common Files\Microsoft
Shared\Web Server Extensions\14\isapi\owssvr.dll” preCondition=”appPoolName=SharePoint Central Administration v4,bitness64” />
I hope would help you resolve your isue 🙂
Reference:
http://blogs.msdn.com/b/govindr/archive/2007/08/30/503-server-unavailable-failure-with-iis-7-0.aspx